Date of Publishing:
HTML Version Coming Soon
Our team is working on an HTML version of this content to enhance usability and compatibility across devices. We aim to make it available in the near future. Thank you for your patience!
Date of Publishing:
Our team is working on an HTML version of this content to enhance usability and compatibility across devices. We aim to make it available in the near future. Thank you for your patience!
Last Updated:
Status:
Published
Review Number:
21-05
Date of Publishing:
Date of Publishing:
| ACRONYM | Description |
|---|---|
| CSIS | Canadian Security Intelligence Service |
| DAG | Data Acquisition and Governance |
| DDO | Deputy Director of Operations |
| DMEX | Data Management and Exploitation |
| ERC | External Review and Compliance |
| FC | Federal Court |
| IC | Intelligence Commissioner |
| JA | Judicial Authorization |
| NSA 2017 | National Security Act 2017 |
| NSIRA | National Security and Intelligence Review Agency |
| ODAC | Operational Data Analysis Center |
| PAD | Publicly Available Dataset |
| PCO | Privy Council Office |
| PS | Public Safety Canada |
| SIRC | Security Intelligence Review Committee |
Approved classes of Canadian datasets. Categories of Canadian datasets approved by the Minister and authorized by the Intelligence Commissioner. The Canadian Security Intelligence Service can only collect and retain a Canadian dataset if it falls under an approved class.
Canadian dataset. A dataset that predominantly relates to individuals within Canada or Canadians.
Dataset. A collection of information stored as an electronic record and characterized by a common subject matter.
Designated employee. An employee designated by the Minister who can carry out one or more activities referred to in sections 11.07 and 11.22, such as evaluating, querying, and exploiting section 11.05 datasets.
Dataset regime. Sections 11.01 to 11.25, 27.1 of the Canadian Security Intelligence Service Act governing datasets.
Evaluation. The period in which designated employees shall, as soon as feasible but no later than the 90th day after the day on which the dataset was collected, evaluate the dataset and confirm if it:
Exigent circumstances. A situation in which there is a danger to the life or safety of an individual or a situation requiring the acquisition of intelligence of significant importance to national security, the value of which would be diminished or lost if the Canadian Security Intelligence Service is required to comply with the authorization process under section 11.13 or sections 11.17 and 11.18.
Exploitation. A computational analysis of one or more datasets for obtaining intelligence that would not otherwise be apparent.
Foreign dataset. A dataset that predominantly relates to individuals who are not Canadians and who are outside Canada or corporations that were not incorporated or continued under the laws of Canada and who are outside Canada.
Judicial Authorization. The process by which a Federal Court judge authorizes the retention of a Canadian dataset.
Minister. In this report, Minister refers to the Minister of Public Safety.
Publicly available dataset. A dataset that was publicly available at the time of collection.
Query. A specific search, with respect to a person or entity, of one or more datasets, for obtaining intelligence.
Section 12 investigations. Investigations carried out by the Canadian Security Intelligence Service that relates to threats to the security of Canada.
Threat to the security of Canada. Activities within or that relate to Canada that involve the following:
The Government of Canada introduced the dataset regime through the National Security Act 2017 (NSA 2017) as a modification to the CSIS Act in July 2019. This regime, constituting sections 11.01-11.25 of the Canadian Security Intelligence Service Act (CSIS Act, hereafter the Act), enables CSIS to collect and retain datasets containing personal information that are not directly and immediately related to activities that constitute a threat to the security of Canada, but are likely to assist in national security investigations.
This review has four sections. The first section, the governance section, describes how CSIS has implemented the regime, CSIS’s first judicial authorization for a Canadian dataset, legislative gaps in the Act, and the department’s internal policies governing the regime. The second section of this review concerns CSIS’s dataset information management and retention practices. The third section concerns how CSIS trains its employees on their dataset regime-related duties and obligations as well as resourcing challenges. Finally, this review includes a case study that encompasses the issues and obstacles related to all of the above-mentioned sections.
In terms of governance and implementation, the National Security and Intelligence Review Agency (NSIRA) found that CSIS’s current application of the dataset regime is inconsistent with the statutory framework. CSIS’s current approach to dataset information collection under section 12 risks the creation of a parallel collection mechanism, one that weakens s.12’s statutory thresholds and simultaneously lacks the external oversight regime intended to protect personal information under the dataset regime.
In 2021, CSIS sought judicial authorization to retain the first Canadian dataset, but in a manner that leads NSIRA to doubt the Federal Court was fully apprised of the internal contradicting views concerning the datasets use prior to the invocation of the dataset regime. Moreover, pending the judicial authorization, CSIS conducted queries pursuant to the exigent circumstances authorization, and retained partial name matches. NSIRA found that the results retained thereof did not meet the strictly necessary threshold applicable for the retention of this information pursuant to section 12 of the Act. NSIRA recommends that CSIS immediately destroy any record containing the names retained pursuant to the exigent circumstances queries, as they do not meet the “strictly necessary” threshold.
This review highlights a gap in the CSIS Act that presents issues as to the governance of foreign datasets. NSIRA notes that the current Act does not provide a time limitation for the Minister, or the Minister’s designate, to authorize the retention of a foreign dataset. Prior to the dataset regime, CSIS collected bulk data that would no longer be compliant pursuant to the new regime. After the dataset regime came into force, CSIS submitted on October 11, 2019, several foreign datasets to the Director, acting as the Minister’s designate. The Intelligence Commissioner (IC) approved the first foreign dataset from this bulk data on December 16, 2020. As of December 2022, CSIS had only submitted two more requests for approval to the IC, totalling three approvals in three years. NSIRA notes that the legislative gap allows the authorization request to remain before the Director, un-actioned for years, and puts into question how CSIS will meet the “likely to assist” threshold and utility of these datasets. NSIRA recommends adding a time limitation for the authorization of a foreign dataset by the Minister or the Minister’s designate.
The final piece on the governance section of this review focuses on the policies CSIS adopted for the dataset regime. NSIRA found that CSIS policies governing publicly available datasets do not contain a requirement for a reasonable expectation of privacy analysis of the collected information. This issue is especially pertinent when considering the strong emerging market for data purchased through data brokers and risks associated with purchasing commercially available information that collectors may have unlawfully collected. NSIRA recommends that CSIS meaningfully analyze and document any possible reasonable expectation of privacy when evaluating publicly available datasets. NSIRA also found that CSIS does not have a policy governing transitory information and that the existing internal directive does not provide employees with sufficient instruction which may result in CSIS retaining information that would otherwise be subject to the dataset regime.
This review’s second section concerns information management and retention of section 11 datasets. From 2018-2019, CSIS conducted an inventory of its holdings to identify information that would be subject to the dataset regime once it came into force. In early 2022, CSIS identified multiple incidents of data, operational reports, and Canadian information extracted from foreign datasets that should have been destroyed. Having identified the non-compliance, CSIS proceeded to implement remedial actions to ensure that any such data is identified and destroyed. In October 2022, NSIRA conducted a search in CSIS’s corporate system and found files containing tens of thousands of entries of Canadian personal information extracted from foreign datasets as well as information amounting to foreign datasets. NSIRA was not provided a satisfactory explanation as to why this information continues to be retained in CSIS’s corporate system or how CSIS distinguishes this information from what it had previously identified as a non-compliance. NSIRA finds that, as of August 2023, CSIS did not comply with the dataset provisions in the CSIS Act because it retained Canadian information extracted from foreign datasets, and foreign information amounting to a dataset.
Moreover, NSIRA did another search in CSIS’s operational repository and found information that would amount to a Canadian dataset. CSIS had not sequestered the operational report, rendering it accessible to all who use the system, contrary to the dataset regime’s retention obligations. NSIRA informed CSIS of this report and was informed it would be treated as a compliance incident. NSIRA again conducted a second search and found another report containing information that would otherwise amount to a Canadian dataset. NSIRA finds that CSIS did not comply with the dataset provisions of the CSIS Act because it retained Canadian information and referenced it as recently as 2022. NSIRA recommends that CSIS immediately destroy Canadian and foreign information found in its corporate and operational repositories that is not strictly necessary to retain. This non-compliant information no longer falls within the legal 90-day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility. NSIRA recommends that CSIS cease to create duplicates of information reported in the operational system and conduct an exhaustive scan of its operational and corporate repositories to identify any non- compliant information.
This review’s third section focuses on training and resourcing. Prior to the coming into force of the dataset regime, CSIS developed and implemented training for the designation of employees pursuant to the dataset regime and mandatory training for all operational employees. NSIRA finds that the training required to become a designated employee to evaluate, query, and exploit section 11 datasets offers clear information on collection and retention requirements. However, NSIRA finds that CSIS operational personnel, including those predominantly dealing with bulk information collection, have not received adequate training allowing them to identify when collected information may fall within the dataset regime. The training is offered on a once-and-done basis for operational employees and contradicts CSIS’s current application of the regime. NSIRA recommends that CSIS develop and deliver scenario-based workshops to train operational personnel on CSIS’s current application of the dataset regime so that they can engage subject matter experts as necessary.
Encompassing all the above-mentioned issues, NSIRA identified a case study that illustrates the challenges CSIS faces in its implementation of the dataset regime. The case involved a dataset containing information regarding thousands of Canadians. NSIRA finds CSIS collected information in relation to activities that could not on reasonable grounds be suspected to have constituted a threat to the security of Canada and the collection, analysis and retention of which was not strictly necessary. The Department of Justice and CSIS managers did not present CSIS executives the totality of information regarding the dataset at the point of collection. The information was also collected absent an analysis of the Charter and privacy considerations. NSIRA recommends that CSIS immediately destroy the case study dataset it collected pursuant to section 12. This information no longer falls within the legal 90-day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility.
The review concludes that CSIS has failed to adequately operationalize the dataset regime. CSIS did not seek to clarify legal ambiguities [**redacted**] of the application of the regime before the Court when given the opportunity to do so. Rather, CSIS has adopted multiple positions on the application of the dataset regime, and now risk limiting what is a collection and retention regime to a retention mechanism. Internally, CSIS has not provided sufficient resources and training to ensure compliance with the regime. Absent an internal commitment to adequately operationalize, resource and support the implementation of a new legal regime, any such regime will fail no matter how fit for purpose it is perceived.
The National Security Intelligence Review Agency (NSIRA) conducted this review pursuant to 8(1)(a) of the National Security Intelligence Review Agency Act.
NSIRA reviewed the Canadian Security Intelligence Service’s (CSIS, or the Service) implementation of the dataset regime between January, 2019 and June 30, 2022. As the review progressed, NSIRA found it necessary to also consider pertinent information outside of this scope.
NSIRA conducted document reviews, interviews, and received briefings. NSIRA also received onsite demonstrations of systems by CSIS subject matter experts. Direct access to these systems was also granted to NSIRA.
NSIRA was able to verify the information it received during the review in a manner that met its internal expectations and requirements. NSIRA had direct access to CSIS systems and repositories, and therefore was able to corroborate information.
With respect to responsiveness, while there were minor instances where CSIS did not provide the totality of the information to NSIRA, overall CSIS met NSIRA’s expectations for responsiveness.
In 2015, the Security Intelligence Review Committee (SIRC), NSIRA’s predecessor, reviewed the collection and retention of information related to CSIS’s Data Acquisition Program. The review examined CSIS’s bulk datasets regime and noted that “SIRC has seen no evidence to suggest that CSIS has systematically taken the CSIS Act s 12 statutory threshold of ‘strictly necessary’ into consideration; CSIS’s lack of process, governance and legal guidance around the acquisition and management of bulk data is lacking and non consistent with the practice of close allies.”
Following the publication of SIRC’s annual report, the Federal Court (hereafter the Court) considered data retention issues in the 2016 “Associated Data” decision. The Court found that CSIS had exceeded the limitations of its legislative mandate by retaining information contrary to the “strictly necessary” limitations prescribed by section 12(1) of the Canadian Security Intelligence Service Act (CSIS Act). Under the “strictly necessary” statutory requirement as applicable to the facts in that judgment, CSIS cannot retain information that is not directly threat-related to the security of Canada unless such information can be related to a warranted target. The Court concluded that CSIS was acting unlawfully when retaining non-threat-related information under the “strictly necessary” qualifier past the warranted time limits.
The Government of Canada introduced the dataset regime through the National Security Act 2017 (NSA 2017) as a modification to the CSIS Act in July 2019. This regime authorizes CSIS to collect datasets that are likely to assist it in its duties and functions; that is, datasets that do not meet the “strictly necessary” otherwise required by s 12.
NSIRA’s review of the dataset regime is the first since the NSA 2017 came into force. This review examines and scrutinizes the governance and operationalization of the regime. In looking at the implementation of the regime, NSIRA also reviews the systems and processes in place for the ingestion, evaluation, query, and exploitation of datasets, a detailed description of which is provided in the Technical Annex A of this report.
The CSIS Act’s (hereafter the Act) provisions governing the regime are found at sections 11.01 to 11.25, 21, 27 & 27.1 of the Act (henceforth referred to as the dataset regime). The Act defines a dataset as a “collection of information stored as an electronic record and characterized by a common subject matter.” The application clause at section 11.02 states that: “Sections 11.01 to 11.25 apply to every dataset that contains personal information, as defined in section 3 of the Privacy Act, that does not directly and immediately relate to activities that represent a threat to the security of Canada.”
The level of authorizations and approvals for collection and retention of a dataset are proportionate with the level of privacy intrusion. For all categories of datasets, publicly available, Canadian, and foreign, CSIS may: “collect the dataset if it is satisfied that the dataset is relevant to the performance of its duties and functions under sections 12 to 16.” An additional, higher threshold exists for the retention of foreign and Canadian datasets where CSIS must establish that the collected dataset is “likely to assist” in the performance of its duties or functions.
The legal framework for the publicly available datasets (PADs), the foreign dataset and Canadian datasets is summarized in the table below:
| Publicly Available | Foreign | Canadian | |
|---|---|---|---|
| Definition | A dataset that was publicly available at the time of collection. | A dataset that predominately relates to individuals who are not Canadians and who are outside Canada or corporations that were not incorporated or continued under the law of Canada who are outside Canada. | A dataset that predominately relates to individuals within Canada or Canadians. |
| Collection | Threshold: Relevant to the performance of duties and functions under s. 12 to s.16 | ||
| Must belong to an approved class authorized by the Minister and approved by the Intelligence Commissioner (IC) | |||
| Evaluation | Within 90 days of the day on which it was collected (no query or exploitation): Designated employee shall delete any personal information that is not relevant to CSIS’s performance of its duties and functions. Designated employee may delete extraneous/erroneous/poor quality information; conduct translation and/or decryption, apply privacy protection techniques; any activity to organize the dataset. | ||
| Designated employee shall delete any information where there is reasonable expectation of privacy that relates to physical or mental health. | |||
| Designated employee to remove any information that relates to a Canadian or person in Canada. | Designated employee to delete any information that is subject to solicitor client privilege. | ||
| Retention | May retain for purposes of s. 12 to s.16. | Threshold: Must be likely to assist in the performance of duties and functions. | |
| Minister or Ministers designate authorize, followed by approval by the IC. | Minister approval followed by application for judicial authorization. | ||
| Retention period | No limitations (internal retention policy) | Maximum 5 years (can reapply) | Maximum 2 years (can reapply) |
| Query/Exploit | May query, exploit, and retain results for s. 12 to 16. | Designated employee may query or exploit (and retain results) to extent that is strictly necessary for s. 12, 12.1, and as required under s. 16. | |
| May query and exploit (and retain results) for s. 15. | |||
| Record Keeping | Record: – rationale for collection; – details of every exploitation; and – details of statutory authority under which query/exploit information is retained. Conduct random and periodic verification | ||
| Must: – Store and manage separately from other information; and – Limit access to designated employees and ensure that information is communicated only for performing duties under the act. | |||
| Exigent Circumstances | Director may authorize (subject to IC approval) the query of a dataset that has not been authorized if there are exigent circumstances that require the query to preserve life of safety of an individual or to acquire intelligence of significant importance to national security the value of which would be diminished or lost if CSIS were too comply with the authorization process. | ||
| Reporting | Report to NSIRA: – Any verification done as required by record keeping provisions. – Removal of information from a foreign dataset that concerns Canadians or persons in Canada. – Copy of the Director’s authorization for exigent circumstances query, the results of the query, and the actions taken after obtaining the results of the query. *NSIRA may report to the Director if it is of the view that query/exploitation of the dataset did not comply with the law. Director to send report along with any additional information to the Federal Court. Federal Court may issue a direction or order or take any other measure considered appropriate | ||
Finding 1: NSIRA finds that CSIS’s current application of the dataset regime is inconsistent with the statutory framework.
Finding 2: NSIRA finds that CSIS’s current approach to dataset information collection under section 12 risks the creation of a parallel collection mechanism, one that weakens section 12’s statutory thresholds and at the same time lacks the external oversight regime intended to protect personal information under the dataset regime.
The dataset regime sought to create a method of allowing the collection and retention of certain information that would not be possible pursuant to section 12 of the CSIS Act. CSIS was actively involved in advocating for this detailed regime and noted during the senate hearings that it (sections 11.01-11.24) was “quite a complex piece of legislation” which required that they work closely with the Department of Justice (hereafter Justice) to examine the “various processes that [they] could employ to make sure” that it was a very “charter compliant regime.” Having been so involved with the drafting of the regime, CSIS was thus well positioned to develop policies and procedures governing the collection, evaluation, query, exploitation and verification of datasets. At issue for CSIS was whether the dataset regime limits collection authorities of datasets under CSIS’s information collection mandates in section 12 (security intelligence), section 15 (security screening investigations), or section 16 (foreign intelligence). CSIS initially adopted the position that, in cases where the dataset was not directly and immediately related to threat activities, it had to be ingested under the section 11.01 regime (hereafter, CSIS’s initial position). This position did not affect the ability to collect information that directly and immediately related to threat activities under section 12.
[**redacted**] CSIS shifted its position to consider the dataset regime as, in effect, subordinate to the collection authorities in sections 12, 15, or 16 of the CSIS Act. In practice, CSIS relies on the dataset regime if and when it has determined that the information falls outside these collection authorities (hereafter, CSIS’s current position). This position reflects an evolution in understanding about the dataset regime’s scope.
CSIS’s application of the dataset regime as reflected in their policies, presentations, and NSA 2017 training materials more closely conformed to their initial position. However, by April 2022, CSIS adopted its current position on the application of the dataset regime, concluding also that the Court supported this interpretation. CSIS now regards the dataset regime as allowing the collection and use (searches) of datasets pursuant to section 12, followed by their retention pursuant to the dataset regime. CSIS has continued to evolve its current position to allow for broader collection and retention under section 12.
Notably, section 12 includes conditions on collection (and retention) that are more demanding than the equivalent thresholds for collection and retention under the dataset regime. Under section 12, an investigation depends on a reasonable grounds to suspect a threat to the security of Canada, and information collection and retention only to the extent “strictly necessary.” The dataset regime, for its part, permits collection where CSIS is “satisfied that the dataset is relevant to the performance of its duties and functions” under sections 12 to 16. Retention of foreign and Canadian datasets is permitted on the threshold of “likely to assist” the enumerated CSIS mandates. Section 12 and the dataset regime also differ in terms of control regimes. CSIS retains under section 12 without any external oversight. Retention under the dataset regime of Canadian datasets requires the Court’s authorization, retention of foreign datasets requires the IC’s approval.
The dataset regime was created for the purpose of broadening carefully-regulated dataset collection and retention in circumstances where the section 12 “strictly necessary” threshold could not be met. NSIRA noted, however, that in the period since the evolution of CSIS’s current position, discussed above, CSIS’s operationalization of the dataset regime and their understanding of the application of the regime seems to have significantly broadened the scope of information captured under its section 12 authorities. This evolution is discussed in the case study at the end of this report.
The [**redacted**] formerly the Data Management and Exploitation or DMEX) is a branch whose primary function is the governance of the dataset regime. By June 2023, CSIS informed NSIRA that [**redacted**] would now move to fully prioritize s. 12 collection over dataset regime collection. CSIS stated that absent a less prescriptive legislative framework for dataset collection, CSIS would not be collecting datasets unless the intention was to exploit them. CSIS then presented NSIRA with a clear example of a foreign dataset within the meaning of the dataset regime and indicated that since there was a possibility that there may be hostile actors on the list, it could be collected pursuant either to section 11.05 of the dataset regime or collected pursuant to s. 12. It could also be searched under section 12, with any threat related search results retained under section 12 and the remainder of the list destroyed.
Two concerns stem from CSIS’s evolving approach to datasets illustrated by the case studies that follow. First, the ingestion of datasets under section 12 may now, in practice, reflect a broadened understanding of the section 12 “reasonable grounds to suspect” and “strictly necessary” thresholds. The standards now invoked to justify the collection and retention of some datasets putatively under section 12, are closer to the “satisfied” and “likely to assist” thresholds for the dataset regime. NSIRA acknowledges that some information meeting the definition of a dataset, i.e. the collection of information stored as an electronic record and characterized by a common subject matter, may fall within section 12 collection and use authorities, e.g. a list of Canadian Extremist Travelers. However, NSIRA’s concerns relate to when s. 12 authorities are interpreted to allow for the collection and use of personal information that is not directly and immediately related to activities that represent a threat to the security of Canada. This approach is inconsistent with the statutory framework and risks the creation of a parallel collection mechanism, one that weakens section 12’s statutory thresholds and at the same time lacks the external oversight regime intended to protect personal information under the dataset regime.
Second, a multi-stage vetting process necessarily follows from an interpretation of the CSIS Act in which the dataset regime applies only where datasets (meeting the section 11.02 definition) cannot be collected or retained under the section 12, 15, or 16 mandates. Not least, there will be a preliminary phase in which CSIS will need to decide which authority applies and whether (because no other collection or retention authority is available) the dataset must be processed under the dataset regime. Without careful guidance, there is a considerable risk of confusion as to what may be done with the dataset during this triage vetting, especially since that vetting process is not expressly anticipated by the Act. It is not clear that the Act accommodates a parallel and separate process in which a dataset is collected under section 12, searched for intelligence purposes, and only then transferred for retention under the dataset regime. This would seem to render the exigent search powers in s 11.22 redundant. While NSIRA was not able to fully confirm the sequence of events, the Canadian dataset judicial authorization case study discussed in the next section reflects the risk of confusion.
Finding 3: NSIRA finds that CSIS failed to fully apprise the Court on their interpretation and application of the dataset regime. CSIS should have sought clarification from the Court as to its views on the precise conduct permissible prior to invocating the dataset regime.
Finding 4: NSIRA finds that when conducting queries in exigent circumstances, CSIS retained information that did not meet the section 12 strictly necessary threshold.
From [**redacted**], CSIS collected [**redacted**] individuals [**redacted**] contained personal information of [**redacted**]. The datasets were provided to CSIS from multiple government [**redacted**] departments [**redacted**]. These datasets were [**redacted**] received by the [**redacted**] Unit and therefore [**redacted**] deemed collected pursuant to s. 12. However, CSIS then sought to retain the pursuant to the dataset regime, requiring authorization by the Federal Court (FC). The result was the first judicial authorization decision under the dataset regime. There are two concerns about the management of this dataset.
In the lead-up to this authorization, there appears to have been considerable uncertainty as to how this dataset might be used. The evidence shows that [**redacted**] received the [**redacted**] through the Security of Canada Information Disclosure Act. [**redacted**] considers all information disclosed and collected by their branch as section 12 information. Upon receipt of the dataset, [**redacted**] was not aware of the discussions occurring within other branches regarding the possibility of applying to the Court for the retention of [**redacted**] through judicial authorization. [**redacted**] treated the information much like any other section 12 information and searched at least two of the names [**redacted**] within CSIS’s operational database, [**redacted**], one of which yielded results.
NSIRA was initially informed that these searches did not amount to queries because they were not searches within the [**redacted**], rather they were searches of names from the [**redacted**] against [**redacted**]. NSIRA was also informed that the searches were not queries because they were not for “the purposes of obtaining intelligence” as defined in the Act, since the results of the searches were not reported [**redacted**]. In [**redacted**] discussion with CSIS, NSIRA received conflicting information that demonstrated internal contradictions and confusion on these points.
In the cover letter to the affidavit for judicial authorization (JA) for a Canadian dataset filed with the Court, Counsel notes that “the Service’s initial collection and use of this information as described in the affidavit falls with the scope of the service’s [**redacted**]. In the affidavit, CSIS stated that “… [**redacted**] verified whether this collection of information was already within Service holdings and assessed the potential intelligence value for its investigations. No searches were conducted for intelligence purposes…” In a previous draft of the affidavit, the chief of DMEX had expressed their concern regarding this wording of the draft affidavit.
They noted that “We have already clearly stated that the datasets were initially collected [**redacted**] authorities. We can also say that checks were done under those authorities but immediately ordered stopped once s.11 was invoked (which happened quickly).” NSIRA could not determine if searches of names from the list against CSIS’s operational system were conducted with the objective of “verifying” whether the “collection of information was already with Service holdings.” In examining this issue, it became apparent that there were multiple opinions and conflicting narratives regarding what actions were taken upon receipt of the dataset and what CSIS perceives as permissible when dataset information is collected through s. 12.
The Federal Court found in its authorization decision that it was reasonable to collect the dataset pursuant to s. 12, in the circumstances of this matter. The Court notes that “the decision was taken to invoke the dataset regime and to request approval to query the information under the exigent circumstances provision in s. 11.22 of the Act.” It is unclear if the Court knew the full record of uncertainty about what could be done with the dataset in the interim between collection under section 12 and the commencement of the dataset regime retention process. CSIS should have fully apprised the Court of this uncertainty (including the conflicting narratives regarding how the data was and may be used) and sought clarification from the Court as to its views on the precise conduct permissible prior to the invocation of the dataset regime.
This is especially the case since, both in the decision and during the hearings for the JA, the Court expressed its concern that the classes authorized by the Minister and approved by the IC were too broad. The Court added that “just about anything under the sun could be captured by one of those classes.” Yet, CSIS assured the Court more than once that information collected was pursuant to s. 11.05 and was protected by the safeguards of the regime, that the information had high access control and could not be queried or exploited. Accordingly, the Court was informed that while the classes are broad, the regime provides the necessary safeguards to protect the privacy of Canadians. This response deemphasized the degree to which information from the dataset might be used during the triage period. Again, this discussion presented CSIS with the opportunity to judicially test its application of the interpretation of the dataset regime before the Court. CSIS could have informed the Court that these safeguards may not necessarily be in place where information is collected pursuant to section 12 prior to a pivot to the dataset regime as the retention authority. It appears that CSIS chose to carry this legal uncertainty at the risk of receiving a constraining interpretation of the regime by the Court.
Notably, once CSIS initiated the dataset regime process, the dataset for which the JA was sought was the subject of an authorization and approval pursuant to s. 11.22 exigent circumstances. CSIS sought and received authorization from the Director and approval from the IC to query the datasets. As per the requirements of section 11.13(2) of the Act, CSIS included in its application for JA the contents of the exigent circumstances authorization, the results of the authorized query, and any actions taken after obtaining these results. This information was also provided to NSIRA as required by s. 11.25(c) of the Act.
CSIS queried the names [**redacted**] CSIS retained [**redacted**] partial matches and reported them in their section 12 operational system. In examining the queries conducted, NSIRA found that the initial searches were extremely broad with many name [**redacted**] searched using extensive use of [**redacted**], and a very large margin for date of birth [**redacted**].
These broad queries resulted in numerous “hits” against the list. For example, [**redacted**] were all considered by the CSIS analyst as appropriate search results against [**redacted**]. These names were then searched in [**redacted**]. Information from an exigent query may be retained if “carried out under section 12”, imposing that section’s “strictly necessary” threshold. Despite there being no results for any of full [**redacted**] names in [**redacted**], CSIS determined that the absence of the names in its operational system meant that the names could not be eliminated as “a possible candidate for identification” and that “ultimately, those possible matches that cannot be excluded will be reported to the desk and retained under s. 12 for further investigation.”28 Similarly, should the name of [**redacted**] be too common to rule out, CSIS retained that name as strictly necessary.
The results of these unnecessarily broad queries did not meet the strictly necessary threshold for retention. [**redacted**] In March 2022, CSIS reported that [**redacted**] has determined it would not pursue investigative steps regarding the results (reported in [**redacted**]) absent additional information” and that the [**redacted**] results retained were “captured in their entirety for retention in the event that the dataset is destroyed.” The exigent circumstances queries cannot be used to circumvent the retention obligations that would apply under s.12 or as means to retain information pending the outcome of the judicial authorization.
Recommendation 1: NSIRA recommends that in the next judicial authorization application for a Canadian dataset CSIS put its current position on the application of the dataset regime before the Court, including any use of the information prior to the decision to retain under the dataset regime.
Recommendation 2: NSIRA recommends that CSIS immediately destroy any record containing names retained pursuant to the exigent circumstances queries as they do not meet the strictly necessary threshold.
Finding 5: NSIRA finds that the lack of explicit time limits in section 11.17 of the dataset provisions governing foreign datasets has resulted in datasets being retained for multiple years pending a decision by the Minister or the Minister’s designate (the CSIS Director).
The dataset regime added many detailed provisions to the CSIS Act. Despite the complexity of the regime, NSIRA noted gaps in the legislation. The provisions of the Act governing the authorization of the retention of foreign datasets do not provide a time limitation for the Minister or the Minister’s designate to authorize the retention of a foreign dataset. Prior to the coming into force of the dataset regime, CSIS had accumulated bulk data that would no longer be compliant pursuant to the new regime. Accordingly, the transitional provisions of Bill C-59 recognized the presence of this information and deemed it collected on July 13, 2019 as per the Order in Council. CSIS then had 90 days to evaluate the foreign datasets it wished to retain, and determine if it wished to evaluate and seek judicial authorization for any bulk Canadian information.
On October 11, 2019, CSIS submitted ten applications for authorization to retain foreign datasets to the Director. The first dataset authorization was approved by the IC on December 16, 2020. In their December 16, 2020, decision, the IC made recommendations regarding the contents of the authorization. One of these recommendations concerned how these datasets collected in [**redacted**] remain likely to assist CSIS in the performance of its duties and functions. The [**redacted**] remaining datasets that had been submitted to the Director for authorization were then edited to include the information requested by the IC. These edits were included as an appendix to the applications. Despite the fact that the edits included material information regarding how the datasets remain likely to assist CSIS in its duties and functions, they were not considered resubmissions to the Director. As of December 2022, CSIS had only submitted two more requests for approval to the IC, totalling three approvals in three years.
CSIS asserted that there were no statutory deadlines that would limit the Director from having these applications for years and that resourcing constraints meant that the requisite edits would take time to complete. This legislative gap has allowed for a parallel mechanism of retention of data that is otherwise strictly governed. While CSIS cannot ingest, query, or exploit the data until the IC approves it, the gap in legislation allows them to query the data in exigent circumstances as per section 11.22 of the CSIS Act.
Furthermore, the legislative gap allowing the authorization request to remain before the Director, un-actioned for years, puts into question how CSIS will meet the “likely to assist” threshold tied to the utility of these datasets. It should be noted that as of April 2023, the dataset approved in 2020 had not been queried, while the one approved in 2021 has been queried only [**redacted**]. This gap in legislation was also noted by the IC, stating: “I am unconvinced that Parliament’s intent was for there to be such a long delay between a request from CSIS for authorization to retain a foreign dataset and the Director’s authorization.”
Recommendation 3: NSIRA recommends that Parliament legislates a time limitation for the authorization of a foreign dataset by the Minister or Minister’s designate.
Finding 6: NSIRA finds that CSIS runs the risk of collecting information that is publicly available but for which there may be a reasonable expectation of privacy.
Finding 7: NSIRA finds that CSIS’s policies governing the collection and retention of Canadian and foreign datasets do not align with its current interpretation of the dataset regime.
Finding 8: NSIRA finds that CSIS does not have a policy governing the handling of transitory information. In addition, the existing Interim Direction [**redacted**] does not provide employees with sufficient instruction, which may result in CSIS retaining information that would otherwise be subject to the dataset regime.
CSIS codified in policy its commitment during the enactment of Bill C-59 to not collect hacked or stolen datasets. It acknowledged that there would be a “much higher expectation of privacy associated with those datasets,” and noted that even if adversaries had access to this information CSIS would hold itself to “a higher standard.” However, overall CSIS found itself struggling to implement the provisions of the Act and align its policies and procedures with it.
NSIRA flags four specific concerns. First, the policy center for datasets is the Data Management and Exploitation Branch (DMEX), recently restructured and renamed as [**redacted**]. The dataset policy suite [**redacted**] includes a number of policies pertaining to the identification, collection and retention of section 11.01 datasets. Although the commitment to not collect stolen, hacked or leaked datasets is codified in [**redacted**], there is no corresponding requirement to ensure that information contained in publicly-available datasets (PADs) does not contain information for which there is a reasonable expectation of privacy. Yet, this requirement is especially pertinent when considering the strong emerging market for data purchased through data brokers and the risks associated with purchasing commercially available information that may have been unlawfully collected by said brokers.
Second, as discussed earlier, the shift in CSIS’s position on the relationship between datasets and its regular collection powers has resulted in discrepancies between what information amounts to s.11.01 datasets and what information may be collected pursuant to s. 12. CSIS’s interpretation of the applicability of the dataset regime was reconsidered in 2021, two years after the dataset governing policies were developed. The existing policy suite aligns more with CSIS’s initial position. This has resulted in a policy suite that no longer aligns with CSIS’s current position on the implementation of the dataset regime (discussed above) or with the current structure of the [**redacted**] branch.
Third, the [**redacted**] policy sought to guide and educate employees on the dataset regime. It also placed the onus on “employees who collect the dataset” to determine the appropriate collection authority. This further emphasizes the importance of training received by employees, discussed further below.
Fourth, in 2021, CSIS developed an Interim Direction to support its section 12 collection of datasets. The introduction of this Direction corresponded with the pivot in the interpretation and operationalization of the dataset regime, discussed in section 4 above. The Direction allows for collection of electronic information that has been assessed to be threat-related where threat and non threat information are inextricably co-mingled. It allows for the temporary retention of this information in these circumstances. The direction does not provide any information as to what amounts to inextricably co-mingled information but allows for its sequestered retention for up to [**redacted**] with extension. This non-threat related information would have been subject to the dataset regime, yet the Direction is silent on the requirements of the dataset regime including the connection and relationship to that regime’s 90 day evaluation period. In practice, CSIS does not have a central repository for temporary information, which results in this information being held on unit shared drives absent centralized monitoring, access controls, and auditing. This, along with the constant rotation of employees, lack of training on the Direction, the absence of clear points of accountability and responsibility in the policy, and the [**redacted**] time limitation which greatly exceeds the 90 days limitation in the dataset regime, creates a situation where CSIS risks retaining depositories of information that would otherwise be subject to the dataset regime.
Recommendation 4: NSIRA recommends that CSIS meaningfully analyze and document any possible reasonable expectation of privacy when evaluating publicly available datasets.
Recommendation 5: NSIRA recommends that CSIS develop:
Finding 9: NSIRA finds that CSIS information management practices are responsible for multiple compliance incidents and currently create duplicates of datasets within CSIS’s systems.
Finding 10: NSIRA finds that, as of August 2023, CSIS did not comply with the dataset provisions in the CSIS Act because it retained Canadian information extracted from foreign datasets, and foreign information amounting to a dataset.
Finding 11: NSIRA finds that CSIS did not comply with the dataset provisions in the CSIS Act because it retained Canadian information and referenced it as recently as 2022. This information should have been destroyed upon coming into force of the NSA 2017, in July, 2019.
Finding 12: NSIRA finds that CSIS has not exhaustively scanned all of its systems to identify information that is subject to the dataset regime so that it may be processed in a compliant manner.
From 2018-2019, CSIS conducted an inventory of its holdings to identify information that would be subject to the dataset regime—and therefore need to be deleted— once the regime came into force. CSIS identified several categories of operational reports containing collected Canadian or Foreign information, and developed caveats to insert into the reports indicating that information had been removed.
For foreign datasets, CSIS senior management identified which foreign datasets would be submitted for authorization. Technical analysts conducted a number of exercises on the foreign datasets to test their ability to identify and extract Canadian information as would be required under the dataset regime. These exercises led to the creation of multiple [**redacted**] containing the extracted Canadian data, which was then uploaded [**redacted**] for storage in CSIS’s corporate repository. In doing so, CSIS retained copies of data that should have been deleted.
According to CSIS, duplication is a requirement of CSIS’s information management policy (see Annex A). For example, when a query of a dataset is conducted, CSIS’s information management policy requires analysts to attach the results of the query to the report that gets saved in the operational system. Analysts are also required to save a copy of that report and its attachments to [**redacted**], CSIS’s corporate repository. This has contributed to compliance issues. It also increases the difficulty of deleting information when compliance incidents arise or if CSIS has retained information that is not strictly necessary. Additional examples of where data duplication occurs are described in Annex A.
On September 5, 2019, CSIS assured the Minister that it “undertook significant efforts to ensure compliance with the coming-into force of the dataset framework created by Bill C-59” and that “as a direct result of this exercise, a number of Canadian and foreign datasets were assessed as not meeting the criteria for retention under section 12 or the `likely to assist’ retention threshold under the new dataset framework. These datasets were therefore destroyed prior to coming-into force.” In September 2021, CSIS asserted to NSIRA that all the foreign datasets that were not before the Director for authorization were destroyed.
In [**redacted**] a former DMEX employee discovered [**redacted**] containing a foreign dataset, which had been collected prior to the coming into force of the dataset regime and subsequently submitted for Ministerial authorization. [**redacted**] contained the entire pre-evaluation dataset, including Canadian information. In [**redacted**] another DMEX employee discovered Canadian information extracted from foreign datasets [**redacted**] accessible only by designated employees. These latter records included Canadian information and foreign samples extracted from [**redacted**] foreign datasets, [**redacted**] of which were pending Ministerial authorization, [**redacted**] of which was already approved by the IC, and of [**redacted**] which were destroyed in their entirety prior to the coming into force of the regime. CSIS destroyed this information because it was unlawfully retained.
These incidents prompted DMEX to conduct a file review “to determine what steps has been taken prior to coming into force of NSA 2017 and what remediation efforts might be necessary. Although employees had been directed to delete potential dataset candidates for which it would not seek authorization to retain with the coming into force of NSA 2017 in July 2019, similar steps had not been taken to direct employees to identify and destroy other copies of datasets and any Canadian or other records removed from these datasets prior to coming into force of NSA 2017 or in the 90 day evaluation period that followed.” DMEX then instructed employees to “conduct a thorough search [**redacted**].” The outcome of these searches was that significant additional Canadian and foreign information was found. This included information pertaining to the [**redacted**] Dataset discussed below. DMEX reported these multiple compliance incidents to CSIS’s review and compliance branch by submitting a fact finding report with supporting material The concluding comments of the report state that a “fulsome” effort was made to identify residual data however [**redacted**] ”.
In October 2022, NSIRA conducted searches of CSIS’s corporate repository and found [**redacted**] files containing tens of thousands of entries of Canadian personal information extracted from [**redacted**] foreign datasets, including information extracted from datasets that have been destroyed, approved by the IC, and pending authorization. The files also contained foreign information. The Canadian information was extracted as part of the exercise to prepare for the coming into force of the Act and should have been destroyed.
NSIRA enquired as to why these files containing Canadian information extracted mostly from destroyed foreign datasets remained in CSIS’s corporate repository and the legal authority under which they are retained. CSIS failed to provide an adequate explanation as to this legal non-compliance, they stated that the information was part of a project in preparation for the coming into force of the dataset regime, and that:
“those Canadian records continue to exist in the PA’d file even though the original datasets were either all destroyed or sequestered pending Ministerial Authorisation. While certainly contrary to current (since June 2019) s.11 obligations, at that time, this work and retention would have been done under (implicit) s.12 authorities. As this predates the dataset framework, we are unclear if this presents a legal or compliance risk. [**redacted**]
CSIS stated that the records were retained “appropriately at the time, pre C-59, under s.12 implicit authorities”. It is unclear how CSIS distinguishes between the information found by NSIRA and that found by DMEX in [**redacted**] mentioned at paragraph 55 above. As of August 2023, information that NSIRA found in October 2022, containing Canadian and foreign data was being retained by CSIS, in contravention of its legal obligations pursuant to the dataset provisions in the CSIS Act.
NSIRA also searched for operational reports that had been identified prior to the coming into force of the dataset regime as containing information that would amount to Canadian datasets. NSIRA found a number of reports where the information had indeed been deleted and a caveat added. However, NSIRA found [**redacted**] report related to [**redacted**] dataset containing the [**redacted**]. It should be noted that the operational report in question was not sequestered, rather was accessible to all those using the system and was referenced in a report as recently as August, 2022. This would have amounted to a query of what should have otherwise been a Canadian dataset.
NSIRA requested that CSIS provide the authorities under which it is retaining this information. CSIS initially responded that they could not find the report as it had been previously destroyed. Shortly thereafter, CSIS stated that they have found the report and were treating it as a compliance incident. Upon searching the operational system once more, NSIRA found another report containing the [**redacted**] Both reports found by NSIRA contained information that would otherwise amount to a Canadian dataset, [**redacted**]. By retaining this Canadian information, CSIS did not comply with legal obligations pursuant to its dataset regime provisions in the CSIS Act.
The non-compliant information found by NSIRA (Canadian and foreign information from foreign datasets and Canadian information in operational reports) was discovered following CSIS’s initial pre C-59 scan of holdings reported to the Minister and following CSIS’s “thorough search of personal and shared holdings” due to the compliance incident in 2022. CSIS has not exhaustively scanned all of its systems to identify information that is subject to the dataset regime so that it may be processed in a compliant manner.
Recommendation 6: NSIRA recommends that CSIS cease to create duplicates of the information reported in the operational system.
Recommendation 7: NSIRA recommends that CSIS immediately destroy Canadian and foreign dataset information that is not strictly necessary to retain. This information no longer falls within the legal 90 day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility.
Recommendation 8: NSIRA recommends that CSIS conduct an exhaustive scan of its operational and corporate repositories to identify and destroy any non-compliant information.
Finding 13: NSIRA finds that the training required to become a designated employee to evaluate, query, and exploit s. 11.01 datasets offers clear information on collection and retention requirements.
Finding 14: NSIRA finds that CSIS operational personnel, including those predominantly dealing with bulk information collection, have not received adequate training allowing them to identify when collected information may fall within the dataset regime.
Prior to the coming into force of the NSA 2017, including the dataset regime, CSIS developed and implemented specialized training for employees to be designated pursuant to s. 11.06(1) of the CSIS Act, and mandatory Bill C-59 training for all operational employees. CSIS also developed and delivered a number of presentations to assistant directors, management, relevant branches, other government departments, and the Federal Court. This suite of training and presentations align with CSIS’s initial position, discussed above, on the applicability of the dataset regime.
CSIS currently offers two mandatory training courses for the designation of employees. These courses emphasize the distinction between s. 12 “strictly necessary” information and what may be collected pursuant to the dataset regime “likely to assist threshold.” The courses require that an employee familiarizes themselves with the standard operating procedures and requirements of the regime. While online training may not be the ideal training method, the training content along with the mix of standard and scenario based questions offered employees clear instruction on the regime and its requirements.
As noted above, CSIS also implemented mandatory training for all operational personnel. CSIS developed most of the dataset regime training prior to and immediately following the coming into force of the NSA 2017. As discussed at Section 4 of this report, CSIS’s understanding of its statutory obligations pursuant to the regime and how these obligations are perceived and implemented, has changed. The result is that the mandatory training received on a once-and-done basis by operational personnel in 2019 does not align with and may in fact contradict CSIS’s current operationalization and implementation of the regime.
Additionally, the very little training that is received by operational personnel does not allow collectors to determine what information is a dataset despite the onus placed on them to do so. This has resulted in individuals who deal with bulk information collection not being sufficiently aware or trained on the dataset regime.
For intelligence officers, CSIS developed a presentation on the dataset regime as part of the [**redacted**], the mandatory course offered to intelligence officers within a few years of their career [**redacted**]. Initially, when CSIS implemented the training program, employees had to work in groups in a series of workshops to identify the properties of s. 11.01 datasets, including distinguishing them from s. 12 datasets and relating Canadian datasets to approved sets of classes. This training was offered as an instructor-led course until March 2020, after which CSIS removed the workshop component from the updated training program, effectively eliminating any scenario-based questions and exercises. While CSIS has told NSIRA that it is currently working on updating the program, the current training offers little opportunity for collectors to distinguish s.11.01 datasets from s. 12 information.
NSIRA finds that CSIS’s once-and-done approach to training on datasets has resulted in a lack of understanding and sensitization of employees to the dataset regime. CSIS should increase its efforts to sensitize its collectors to the dataset regime requirements and particularities while encouraging them to contact the data exploitation branch when in doubt.
Recommendation 9: NSIRA recommends that CSIS develop and deliver scenario-based workshops to train operational personnel on CSIS’s current application of the dataset regime so that they can engage subject matter experts as necessary.
Finding 15: NSIRA finds that CSIS has not prioritized resourcing the technical unit responsible for the evaluation, query and exploitation of Canadian and foreign datasets.
Finding 16: NSIRA finds that CSIS has not devoted sufficient resources to improving the current technical systems or developing new ones that are equipped to support bulk data use.
In NSIRA’s past review work, issues of training and resourcing often arise together and correlate to an organization’s commitment to a particular program or branch. In April and in November 2022, CSIS informed NSIRA that the Operational Data Analysis Center (ODAC), housed within DMEX and responsible for the technical implementation of the dataset regime including the ingestion, query, and exploitation of datasets was [**redacted**] percent vacancy respectively.
In 2020, no employees were designated for the query or exploitation of datasets despite the authorization and approval of the first foreign dataset. CSIS’s approach to ensuring that they have individuals who are designated and therefore lawfully able to query and exploit information was reactive. In a 2020 verification report provided to NSIRA, CSIS stated that first foreign dataset was authorized by the Director and approved by the IC, yet “there were no employees designated for queries of exploitation of s. 11 Canadian or foreign datasets.
Consequently, no queries or exploitations” of the dataset were conducted. The fact that CSIS had sent its first dataset approval to the IC without having resourced its specialized unit and enabled them to conduct the potential requisite queries and exploitation of the dataset is indicative of [**redacted**]. It took CSIS almost [**redacted**] years to designate an employee for query and exploitation of foreign and Canadian datasets. With the exception of the queries conducted pursuant to the exigent circumstances, no other queries were conducted in 2021.
In November 2022, CSIS expressed concerns that the 90 days provided for evaluation in the Act is too inhibiting and has often resulted in missed collection opportunities. [**redacted**]. Upon further discussion NSIRA was informed that [**redacted**]. Similarly, in 2023 NSIRA was again informed of CSIS’s inability to work within the parameters of the current legislation; in this instance, CSIS had greater resources but had chosen to allocate them to [**redacted**] collection rather than the dataset regime.
The resourcing issues are further compounded by CSIS’s current technical ecosystem. The lifecycle of a dataset involves many different digital tools and systems, [**redacted**] Moreover, these tools and systems can only be customized and maintained by people with niche technical expertise. These compounding factors have created a situation where DMEX employees have limited options for conducting data exploitation, and this has affected the utility of all three categories of datasets. Based on briefings with technical experts and technical demonstrations, it is evident that the current systems are not designed to support bulk data use in a compliant manner.
Recommendation 10: NSIRA recommends that CSIS prioritize resourcing the technical unit responsible for the evaluation, query and exploitation of Canadian and foreign datasets.
Recommendation 11: NSIRA recommends that CSIS prioritize the improvement of current technical systems or development of new systems, equipped to support compliant bulk data use.
Finding 17: NSIRA finds that CSIS collected information in relation to activities that could not on reasonable grounds be suspected to have constituted a threat to the security of Canada and the collection, analysis and retention of which was not strictly necessary.
[**redacted**]
[**redacted**]
On [**redacted**], CSIS sent a brief to the Privy Council Office and Public Safety outlining the information in [**redacted**] noting that prior [**redacted**].
CSIS [**redacted**]. The brief discusses the possibility of collecting the dataset under section 11, utilizing the 90-day evaluation period to assess whether it is a publicly available or Canadian dataset, and “if retaining and using the dataset for analysis will help ensure the security of Canada.”
The following day, [**redacted**].
[**redacted**], the Director General of the Data Management and Exploitation branch and of [**redacted**] submitted a co-drafted Memo to the Deputy Director of Operations (DDO) seeking the authorization to collect [**redacted**] pursuant to section 12 of the CSIS Act. The memo provides a summary of [**redacted**]. The memo notes [**redacted**] concerns regarding [**redacted**]. While the memo outlines the contents of the dataset as described [**redacted**], it fails to mention [**redacted**] within the database [**redacted**] likely stolen.
The memo quotes [**redacted**]. This statement again contradicts [**redacted**] assessment that information was likely collected for [**redacted**]. Based on that statement, the memo argues: [**redacted**].
Upon receipt of the memo, the DDO requests [**redacted**] ” In response, the DDO notes her concerns that [**redacted**] found no evidence suggesting that the [**redacted**]. The DDO further states that she will accept that the information “may indeed assist” CSIS’s investigation and that while no evidence of [**redacted**], “it is more likely than not” that this is the type of information [**redacted**] “would be interested in.” The DDO approved the collection pursuant to section 12 [**redacted**], CSIS received and ingested the Canadian [**redacted**].
[**redacted**]” It is unclear how this assessment was made, as it does not align with CSIS’s analysis of the [**redacted**], which was used to develop a CSIS Case Report, circulated to partners in government. The report states: “the portion of the dataset referencing Canadians appears [**redacted**]. The brief further notes that [**redacted**]. It should be noted that following the distribution of the Case Analysis Brief, CSIS has not conducted any further intelligence analysis or reporting on the dataset.
When CSIS became aware of [**redacted**], the initial discussions focused on the potential collection of the information pursuant to the dataset regime provisions and utilizing the 90 day evaluation period to determine the scope of the dataset, whether it would be a Canadian, foreign, or publicly available dataset. It remains unclear to NSIRA why or what led the discussion to focus instead on a section 12 collection.
At the point of collection, CSIS had limited information regarding the dataset. Much of this information was also conflicting. [**redacted**]. Unfortunately, the full scope of this information was not presented to the DDO when seeking approval for collection pursuant to s.12.
Section 12 of the CSIS Act requires that “The Service shall collect by investigation or otherwise, to the extent that is strictly necessary, and analyse and retain information and intelligence respecting activities that may on reasonable grounds be suspected of constituting threats to the security of Canada.” The threshold to be met is reasonable grounds to suspect. The Supreme Court of Canada has defined a reasonable suspicion as “something more than mere suspicion and something less than a belief based upon reasonable and probable grounds.” It is a “robust standard,” which is “determined by the totality of the circumstances based on the objectively discernable facts.”
Applying the Supreme Court of Canada’s jurisprudence regarding the reasonable suspicion standard to the case at hand, CSIS did not provide any evidence or intelligence to support that the information [**redacted**]. In its analytical tools [**redacted**]. NSIRA found no evidence to support this statement at the point of collection, nor could CSIS explain how they reached said conclusion. That is to say, there were no objectively discernable facts to support that the dataset was indeed connected to a threat to the security of Canada. Rather, CSIS’s explanations to NSIRA, as well as the written records, focus on the potential utility of the information [**redacted**]. CSIS could not provide sufficient evidence to demonstrate how the collection of the information would be strictly necessary pursuant to s. 12. This is best articulated by the DDO’s comments stating that she is “not sold on the rationale” presented to her in the briefing note, but that she was convinced that given the importance of such information to [**redacted**] “it may indeed assist our [**redacted**] investigation of the threat represented [**redacted**]” NSIRA does contend that the information may be of use to [**redacted**] and the analysis of the dataset may be of use to CSIS. However, this dataset does not meet the strictly necessary threshold. Rather, it may meet the s. 11.05 threshold of “relevant to the performance of its duties and functions.”
Furthermore, the CSIS memo to the DDO did not disclose [**redacted**] belief that some of the information was not publicly available and that [**redacted**] may have been “stolen” [**redacted**]. Instead, it focused on [**redacted**]. The memo drafters used [**redacted**] statements to support their belief that there were ties to threat actors [**redacted**]. [**redacted**]. There was no preliminary assessment conducted by CSIS of the dataset as they did not have access to it. [**redacted**] stated [**redacted**] likely “stolen.”. Yet, there was no analysis of the privacy implications of the collection, nor an analysis on whether the collection of this dataset pursuant to section 12 may require a warrant.
Upon collection of the information CSIS analysed the dataset. It should be emphasized that this would have amounted to an exploitation of what should have otherwise been a Canadian dataset.
[**redacted**] the Data Management and Exploitation branch engaged [**redacted**] on the issue of retention of the dataset in light of the requirements in the policy.
[**redacted**]. This statement directly contradicts CSIS’ own assessment of the dataset, which states that [**redacted**]. It proceeds to justify retention by noting that [**redacted**].
A plain dictionary reading of the words “strictly necessary” in s. 12 of the CSIS Act would render a requirement that the information be “rigidly” “indispensable.” However, CSIS did not demonstrate in its justification how the information in the dataset is indispensable to its investigation. Rather, there is a “just in case” type argument put forward that states that it is important to retain the information as it could help a future targeting trend analysis. This justification may meet a likely to assist threshold but does not meet a strictly necessary threshold.
CSIS informed NSIRA that there has been no decision regarding the retention of the dataset, [**redacted**]. NSIRA also learned that should another relevant dataset or associated information arise in the future, at that point [**redacted**]. The dataset is currently in a controlled access shared drive, however no measures are in place to prevent its duplication or movement to other locations.
Recommendation 12: NSIRA recommends that CSIS immediately destroy the case study dataset it collected pursuant to section 12 as it does not meet the statutory thresholds. This information no longer falls within the legal 90 day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility.
In its annual classified report to the Minister, CSIS stated “When considering the challenges with both the exigent circumstances and normal applications of the dataset regime, it is clear that as currently designed, the regime is incapable of managing the volume and variety of data needed to build a robust and sustainable data analytics program, while maintaining Parliament’s intended control and oversight.”
Having been so involved with the drafting of the regime, CSIS was well positioned to develop policies and procedures governing the collection, evaluation, query, exploitation and verification of datasets. NSIRA expected to find a more mature and compliant application of the dataset regime.
As discussed in this report, CSIS has failed to adequately operationalize the dataset regime. While the regime is indeed complex, CSIS has not sought to clarify legal ambiguities [**redacted**] of the application of the regime before the Court when given the opportunity to do so. Rather, CSIS has adopted multiple positions on the application of the dataset regime that risk limiting what is a collection and retention regime to a retention mechanism. Internally, CSIS has not devoted sufficient resources to ensure compliance to the regime, this extends beyond the compliance incidents noted in this report and includes a lack of dedicated technical experts and systems capable of handling and exploiting bulk data. Nor has CSIS devoted adequate resources to sensitizing its employees to the requirements of the regime through training. Absent appropriate training and internal commitment to adequately resource and support the implementation of a new legal regime, any such regime will fail no matter how fit for purpose it is perceived.
Recommendation 13: NSIRA recommends that CSIS share the full unredacted copy of this report with the Federal Court.
This annex describes the technical processes and systems involved with CSIS’s identification, collection, evaluation, retention, querying, exploitation, ingestion, and destruction of Section 11.01 datasets. CSIS uses similar processes and systems for all Canadian and Foreign datasets. The following description of the technical processes and systems involved with the lifecycle of s.11.01 datasets stems from CSIS briefings delivered on 12 May 2022 and 3 October 2022, a technical demo delivered on 1 November 2022, as well as from the policy suite that governs the collection, evaluation and retention of s.11.01 datasets. This annex should be seen as reflective of the technical processes and systems in place until the end of this report’s review period.
Because datasets are defined by Section 2 of the CSIS Act as “a collection of information stored as an electronic record and characterized by a common subject matter,” the scope and breadth of what may be considered a ‘dataset’ is considerable. Some of the technical challenges that CSIS encounters with datasets stem from the variety of data types [**redacted**], and sizes of files [**redacted**] that can comprise a ‘dataset’.
SIS acknowledges that “while comprehensive, there remains residual risk in these complex systems. They are manual, resource-intensive and subject to error. They reflect the complexity of the datasets regime, and offer limited resilience and scalability.”
S.11.01 datasets can be identified and collected by CSIS in a number of ways. For example, Service employees can receive datasets from national and international partners or informants via email, USB drives, external hard drives, or other data storage devices. CSIS employees can [**redacted**], encounter a dataset while performing searches on the internet, [**redacted**]. These diverse processes involve any number of technical processes and systems depending on how, where, and by whom the datasets are identified and collected.
DMEX has centralized the s.11.01 dataset evaluation process; one of DMEX’s designated employees must evaluate the dataset within 90 days of its initial collection. During this 90 day period, a designated employee must determine if the dataset meets the requirements for retention as either a Canadian or foreign dataset. The technical processes and systems involved with the evaluation phase vary depending on the format(s), size(s), and location(s) of the dataset. [**redacted**]. Each dataset must be evaluated using techniques and tools suitable to its unique characteristics. If CSIS initially collected multiple versions of the same dataset, DMEX is responsible for ensuring that all other copies of the dataset have been deleted from Service systems.
If the evaluation results lead DMEX to attempt to retain a Canadian or foreign dataset, CSIS must proceed with the requisite applications for approval and authorization. The systems and programs used to develop materials submitted for approvals and authorizations often lead to the creation of substantial documentation (e.g. memos, briefing notes, and affidavits prepared in Microsoft Word or Excel) describing the datasets. In some cases, copies or subsets of information from the datasets are included in the materials submitted for approval and authorization.
To manage and track a dataset’s evaluation workflow, [**redacted**]. For each dataset it evaluates, DMEX [**redacted**].
Once a Canadian or foreign dataset has been approved for retention, it is ingested [**redacted**], which is CSIS’s [**redacted**] enables CSIS to store and aggregate all of their operational information and datasets, apply access controls to that information, and perform all requisite security logging processes.
All information ingested into [**redacted**] assigned attribute-based access controls that are mapped to CSIS’s [**redacted**] for designated employees who are evaluating a dataset and [**redacted**] for designated employees who can query and exploit the retained datasets. No other employees can access the datasets.
When employees access datasets, CSIS uses [**redacted**] to collect and index information about what they are doing. CSIS collects [**redacted**].
[**redacted figure**]
Figure 1: Map of [**redacted**] for querying and exploiting foreign and Canadian datasets.
Only ‘designated employees’ can query and exploit Canadian or foreign datasets, and DMEX has centralized these processes. When a Service employee wants to query a s.11.01 dataset in support of an investigation, they must submit a [**redacted**] to DMEX [**redacted**] . Alongside this request, [**redacted**] The information supplied in each [**redacted**] is used to select the appropriate “justification” when a designated DMEX Analyst performs queries or exploitations [**redacted**] or [**redacted**]. [**redacted**]
If the DMEX analyst finds any results from their queries or exploitations, they record [**redacted**]. They must then contact [**redacted**]. [**redacted**]. This manual set of processes creates multiple copies of raw data from datasets, which can be unintentionally retained on Service employees’ desktop computers or in their email sent/received folders.
[**redacted**] Data is compartmentalized (s.12, s.15, s.16, s.17) based on an investigation’s [**redacted**] and retained as per the [**redacted**] rules associated with it.
[**redacted**] CSIS’s corporate repository. This leads to further duplication of raw data from s.11.01 datasets within CSIS’s digital ecosystem.
When datasets are initially ingested into [**redacted**], they are assigned a retention period based on whether they are Canadian or foreign. When that retention period ends, [**redacted**].
| Date | Subject |
|---|---|
| Briefings: | |
| February 17, 2021 | Publicly Available Datasets. |
| September 9, 2021 | Foreign Datasets. |
| April 22, 2022 | CSIS Dataset Regime. |
| May 12, 2022 | [**redacted**] Evaluation, Query, Exploitation, Retention & Reporting of Canadian and Foreign Datasets. |
| October 3, 2022 | [**redacted**] |
| November 1, 2022 | Technical Demonstration on Dataset Systems. |
| [**redacted**] | Case Study Briefing. |
| June 6, 2023 | [**redacted**] |
| Interviews: | |
| August 18, 2022 | Canadian dataset. |
| September 6, 2022 | Canadian dataset. |
| October 14, 2022 | Canadian dataset. |
| October 21, 2022 | Canadian dataset. |
| Finding 1: NSIRA finds that CSIS’s current application of the dataset regime is inconsistent with the statutory framework. | Recommendation 1: NSIRA recommends that in the next judicial authorization application for a Canadian dataset CSIS put its current position on the application of the dataset regime before the Court, including any use of the information prior to the decision to retain under the dataset regime. |
| Finding 2: NSIRA finds that CSIS’s current approach to dataset information collection under section 12 risks the creation of a parallel collection mechanism, one that weakens section 12’s statutory thresholds and at the same time lacks the external oversight regime intended to protect personal information under the dataset regime. | |
| Finding 3: NSIRA finds that CSIS failed to fully apprise the Court on their interpretation and application of the dataset regime. CSIS should have sought clarification from the Court as to its views on the precise conduct permissible prior to invocating the dataset regime. | |
| Finding 4: NSIRA finds that when conducting queries in exigent circumstances, CSIS retained information that did not meet the section 12 strictly necessary threshold. | Recommendation 2: NSIRA recommends that CSIS immediately destroy any record containing names retained pursuant to the exigent circumstances queries, as they do not meet the strictly necessary threshold. |
| Finding 5: NSIRA finds that the lack of explicit time limits in section 11.17 of the dataset provisions governing foreign datasets has resulted in datasets being retained for multiple years pending a decision by the Minister or Minister’s designate (the CSIS Director). | Recommendation 3: NSIRA recommends that Parliament legislates a time limitation for the authorization of a foreign dataset by the Minister or Minister’s designate. |
| Finding 6: NSIRA finds that CSIS runs the risk of collecting information that is publicly available but for which there may be a reasonable expectation of privacy. | Recommendation 4: NSIRA recommends that CSIS meaningfully analyze and document any possible reasonable expectation of privacy when evaluating publicly available datasets. |
| Finding 7: NSIRA finds that CSIS’s policies governing the collection and retention of Canadian and foreign datasets do not align with its current interpretation of the dataset regime. | Recommendation 5: NSIRA recommends that CSIS develop:
|
| Finding 8: NSIRA finds that CSIS does not have a policy governing the handling of transitory information. In addition, the existing Interim Direction on [**redacted**] does not provide employees with sufficient instruction, which may result in CSIS retaining information that would otherwise be subject to the dataset regime. | |
| Finding 9: NSIRA finds that CSIS information management practices are responsible for multiple compliance incidents and currently create duplicates of datasets within CSIS’s systems. | Recommendation 6: NSIRA recommends that CSIS cease to create duplicates of the information reported in the operational system. |
| Finding 10: NSIRA finds that, as of August 2023, CSIS did not comply with the dataset provisions in the CSIS Act because it retained Canadian information extracted from foreign datasets, and foreign information amounting to a dataset. | Recommendation 7: NSIRA recommends that CSIS immediately destroy Canadian and foreign dataset information that is not strictly necessary to retain. This information no longer falls within the legal 90 day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility. |
| Finding 11: NSIRA finds that CSIS did not comply with the dataset provisions in the CSIS Act because it retained Canadian information and referenced it as recently as 2022. This information should have been destroyed upon coming into force of the NSA 2017, in July, 2019. | |
| Finding 12: NSIRA finds that CSIS has not exhaustively scanned all of its systems to identify information that is subject to the dataset regime so that it may be processed in a compliant manner. | Recommendation 8: NSIRA recommends that CSIS conduct an exhaustive scan of its operational and corporate repositories to identify and destroy any non-compliant information. |
| Finding 13: NSIRA finds that the training required to become a designated employee to evaluate, query, and exploit section 11.01 datasets offers clear information on the collection and retention requirements. | Recommendation 9: NSIRA recommends that CSIS develop and deliver scenario-based workshops to train operational personnel on CSIS’s current application of the dataset regime so that they can engage subject matter experts as necessary. |
| Finding 14: NSIRA finds that CSIS operational personnel, including those predominantly dealing with bulk information collection, have not received adequate training allowing them to identify when collected information may fall within the dataset regime. | |
| Finding 15: NSIRA finds that CSIS has not prioritized resourcing the technical unit responsible for the evaluation, querying, and exploitation of Canadian and foreign datasets. | Recommendation 10: NSIRA recommends that CSIS prioritize resourcing the technical unit responsible for the evaluation, querying, and exploitation of Canadian and foreign datasets. |
| Finding 16: NSIRA finds that CSIS has not devoted sufficient resources to improving the current technical systems or developing new ones that are equipped to support bulk data use. | Recommendation 11: NSIRA recommends that CSIS prioritize the improvement of current technical systems or development of new systems, equipped to support compliant bulk data use. |
| Finding 17: NSIRA finds that CSIS collected information in relation to activities that could not on reasonable grounds be suspected to have constituted a threat to the security of Canada and the collection, analysis, and retention of which was not strictly necessary. | Recommendation 12: NSIRA recommends that CSIS immediately destroy the case study dataset it collected pursuant to section 12, as it does not meet the statutory thresholds. This information no longer falls within the legal 90 day evaluation period and retaining it pursuant to the dataset regime is no longer a possibility. |
| Recommendation 13: NSIRA recommends that CSIS share the full unredacted copy of this report with the Federal Court. | |
Last Updated:
Status:
Published
Review Number:
21-15
Date of Publishing:
The National Security and Intelligence Committee of Parliamentarians Secretariat (NSICOP);
The National Security and Intelligence Review Agency Secretariat (NSIRA) (“the Participants”).
In light of section 9 of the NSICOP Act and section 13 of the NSIRA Act, the Participants intend to cooperate as follows:
1.1 The objectives of this Memorandum of Understanding (MOU) are to:
1.2 The contents of this MOU do not preclude the development of other collaborative initiatives to meet objectives other than those described in paragraph 1.1.
2.1 Each Participant is represented by the Secretariat’s Executive Director, who will sign this MOU and any subsequent amendment to this MoU.
2.2 For the purposes of administering this MOU, the Participants’ designated representatives are:
3.1 The Participants will meet at least once annually to discuss their respective review body’s review planning cycle and other relevant topics.
3.2 The designated representatives, or their delegates, will also consult with each other:
3.3 Any record of decisions between the Participants will be documented as determined by the Participants at the time of the consultation or meeting.
4.1 The Participants agree to maintain open channels of communication in order to identify as early as possible matters where it would be useful to cooperate or to share information to avoid unnecessary duplication in pursuit of their respective mandates.
4.2 Each Participant will share information with the other Participant as necessary to meet the objectives of their respective enabling statutes.
4.3 The review bodies must cooperate to avoid unnecessary duplication in the fulfilment of their respective mandates. This includes:
Procedure for providing information to the other Participant under this MOU.
4.4 A Participant may, on its own initiative or on request, provide information to the other Participant.
4.5 Requests for information should be sent by a Participant’s designated representative to the designated representative of the other Participant. The request must include the following:
4.6 The Participants will keep internal records on information that is shared.
4.7 Both Participants will inform and consult with relevant departments and agencies prior to requesting, or sharing on their own initiative, any information obtained from those departments or agencies. This will provide implicated departments and agencies the opportunity to review the reports for compliance with section 14 of the NSICOP Act or to invoke subsection 16(1) of the NSICOP Act.
5.1 The Participants agree to maintain appropriate safeguards to protect information and records obtained or created under this MOU, and to act in accordance with applicable federal legislation, policies and guidelines regarding their collection, retention, use, disclosure and disposal.
5.2 For greater certainty, the Participants agree that
6.1 In cases where a Participant receives any request from a third party for access to, or disclosure of, information or documents received from the other Participant, it will notify the other Participant as soon as practicable to enable NSICOP to invoke section 16.6 of the Access to Information Act, if applicable.
7.1 This MOU takes effect on the date of the last signature.
7.2 This MOU may be amended at any time with the written consent of the Participants.
7.3 This MOU is not intended to be legally binding or judicially enforceable.
7.4 Either Participant may terminate this MOU by giving the other Participant at least 30days’ written notice.
7.5 In the spirit of cooperation, the Participants agree that any dispute arising under this MOU will be resolved through informal discussions at the appropriate level.
The undersigned have signed this MOU in the English and French languages and both versions are equally authoritative.
Date of Publishing:
This quarterly report has been prepared by management as required by section 65.1 of the Financial Administration Act and in the form and manner prescribed by the Directive on Accounting Standards, GC 4400 Departmental Quarterly Financial Report. This quarterly financial report should be read in conjunction with the 2023–24 Main Estimates.
This quarterly report has not been subject to an external audit or review.
The National Security and Intelligence Review Agency (NSIRA) is an independent external review body that reports to Parliament. Established in July 2019, NSIRA is responsible for conducting reviews of the Government of Canada’s national security and intelligence activities to ensure that they are lawful, reasonable and necessary. NSIRA also hears public complaints regarding key national security agencies and their activities.
A summary description NSIRA’s program activities can be found in Part II of the Main Estimates. Information on NSIRA’s mandate can be found on its website.
This quarterly report has been prepared by management using an expenditure basis of accounting. The accompanying Statement of Authorities includes the agency’s spending authorities granted by Parliament and those used by the agency, consistent with the 2023–24 Main Estimates. This quarterly report has been prepared using a special-purpose financial reporting framework (cash basis) designed to meet financial information needs with respect to the use of spending authorities.
The authority of Parliament is required before money can be spent by the government. Approvals are given in the form of annually approved limits through appropriation acts or through legislation in the form of statutory spending authorities for specific purposes.
This section highlights the significant items that contributed to the net increase or decrease in authorities available for the year and actual expenditures for the quarter ended September 30, 2023.
NSIRA Secretariat spent approximately 33% of its authorities by the end of the second quarter, compared with 23% in the same quarter of 2022–23 (see graph 1).
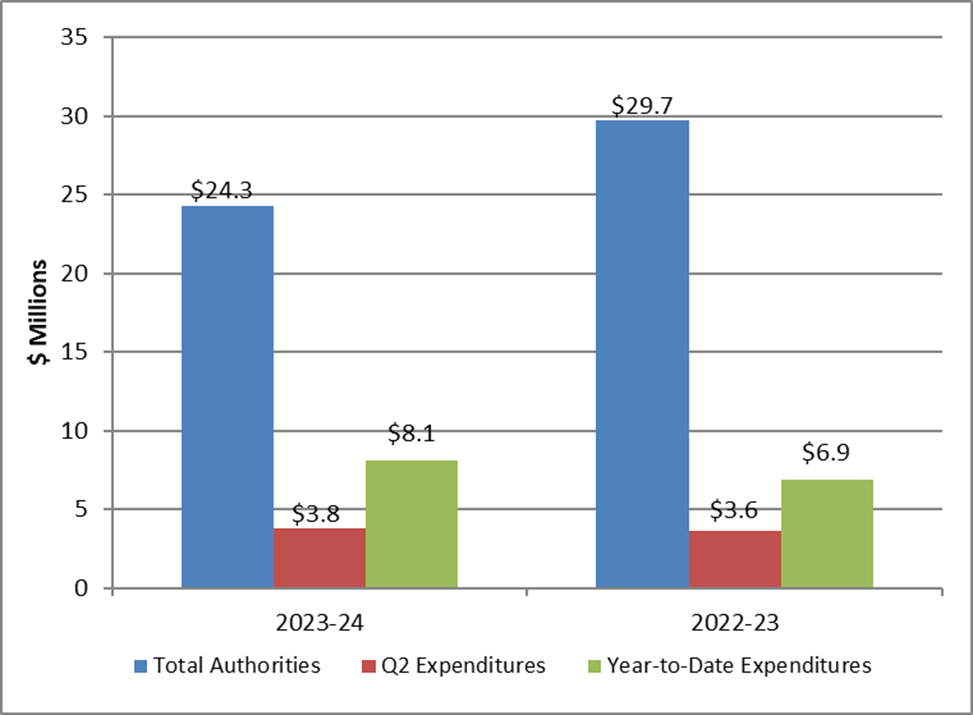
| 2023-24 | 2022-23 | |
|---|---|---|
| Total Authorities | $24.3 | $29.7 |
| Q2 Expenditures | $3.8 | $3.6 |
| Year-to-Date Expenditures | $8.1 | $6.9 |
As at September 30, 2023, Parliament had approved $24.3 million in total authorities for use by NSIRA Secretariat for 2023–24 compared with $29.7 million as of September 30th, 2022, for a net decrease of $5.4 million or 18.2% (see graph 2).
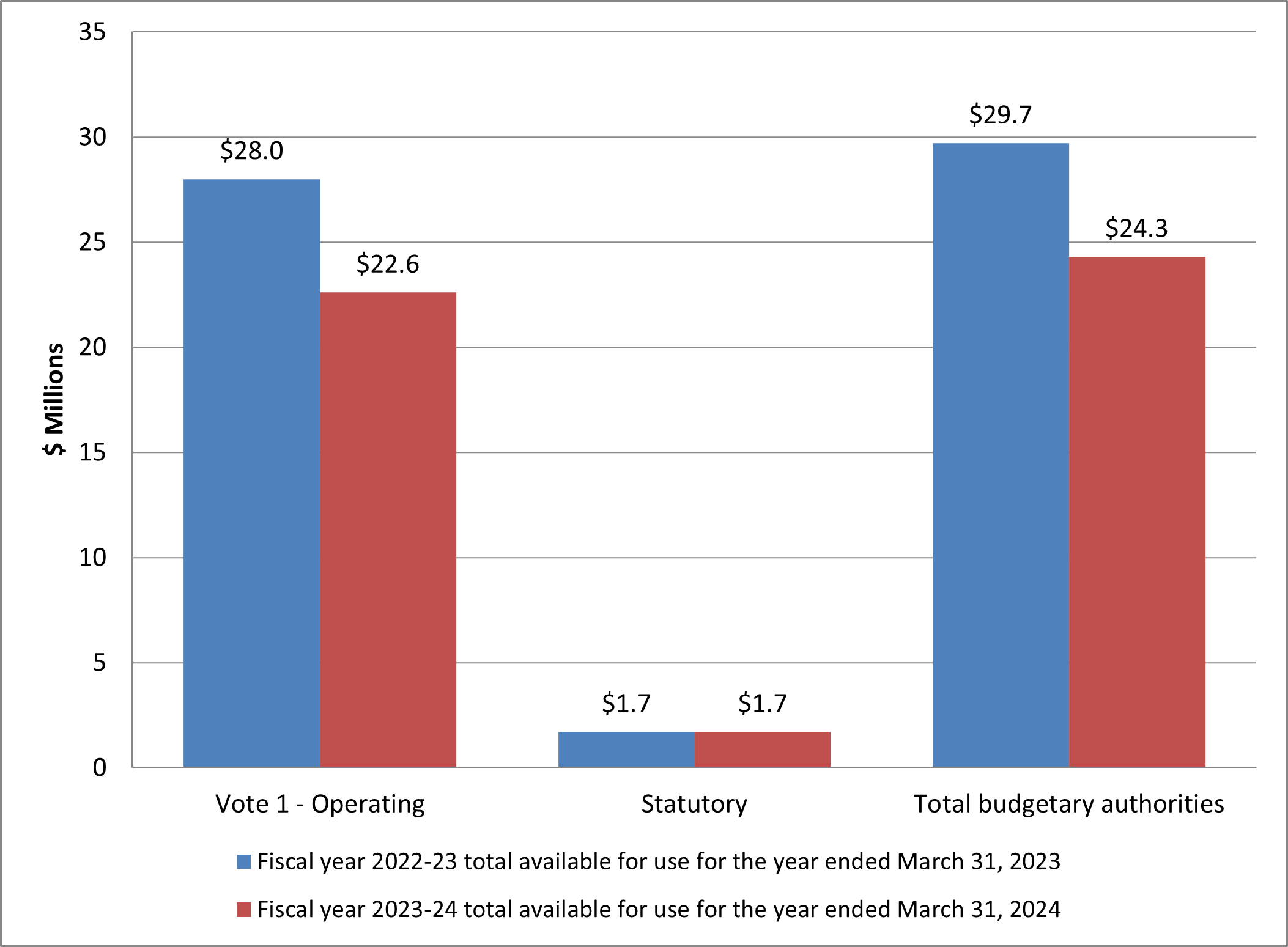
| Fiscal year 2022-23 total available for use for the year ended March 31, 2023 | Fiscal year 2023-24 total available for use for the year ended March 31, 2024 | |
|---|---|---|
| Vote 1 – Operating | 28.0 | 22.6 |
| Statutory | 1.7 | 1.7 |
| Total budgetary authorities | 29.7 | 24.3 |
*Details may not sum to totals due to rounding*
The decrease of $5.4 million in authorities is mostly explained by a gradual reduction in NSIRA Secretariat’s ongoing operating funding due to an ongoing construction project nearing completion.
The second quarter expenditures totalled $3.8 million for an increase of $0.2 million when compared with $3.6 million spent during the same period in 2022–2023. Table 1 presents budgetary expenditures by standard object.
| Variances in expenditures by standard object(in thousands of dollars) | Fiscal year 2023–24: expended during the quarter ended September 30, 2023 | Fiscal year 2022–23: expended during the quarter ended September 30, 2022 | Variance $ | Variance % |
|---|---|---|---|---|
| Personnel | 3,014 | 2,903 | 111 | 4% |
| Transportation and communications | 62 | 70 | (8) | (11%) |
| Information | 4 | 0 | 4 | 100% |
| Professional and special services | 504 | 578 | (74) | (13%) |
| Rentals | 25 | 39 | (14) | (36%) |
| Repair and maintenance | 3 | 33 | (30) | (91%) |
| Utilities, materials and supplies | 50 | 12 | 38 | 317% |
| Acquisition of machinery and equipment | 4 | 4 | 0 | 0% |
| Other subsidies and payment | 118 | 3 | 115 | 3833% |
| Total gross budgetary expenditures | 3,784 | 3,642 | 142 | 4% |
The decrease of $30,000 is due to the timing of invoicing for an ongoing capital project.
The increase of $38,000 is due to a temporarily unreconciled suspense account.
The increase of $115,000 is explained by an increase in payroll system overpayments which were subsequently resolved.
The year-to-date expenditures totalled $8.1 million for an increase of $1.1 million (17%) when compared with $6.9 million spent during the same period in 2022–23. Table 2 presents budgetary expenditures by standard object.
| Variances in expenditures by standard object(in thousands of dollars) | Fiscal year 2023–24: year-to-date expenditures as of September 30, 2023 | Fiscal year 2022–23: year-to-date expenditures as of September 30, 2022 | Variance $ | Variance % |
|---|---|---|---|---|
| Personnel | 5,900 | 5,248 | 652 | 12% |
| Transportation and communications | 192 | 114 | 78 | 68% |
| Information | 4 | 5 | (1) | (20%) |
| Professional and special services | 1,669 | 1,424 | 245 | 17% |
| Rentals | 73 | 49 | 24 | 49% |
| Repair and maintenance | 27 | 64 | (37) | (58%) |
| Utilities, materials and supplies | 57 | 28 | 29 | 104% |
| Acquisition of machinery and equipment | 52 | 13 | 39 | 300% |
| Other subsidies and payment | 122 | 1 | 121 | 12100% |
| Total gross budgetary expenditures | 8,096 | 6,946 | 1,150 | 17% |
The increase of $652,000 relates to an increase in average salary and an increase in full time equivalent (FTE) positions.
The increase of $78,000 is due to the timing of invoicing for the organization’s internet connections.
The increase of $245,000 is explained by an increase in IT support costs and guard services associated to a capital construction project.
The decrease of $37,000 is due to the timing of invoicing for an ongoing capital project.
The increase of $29,000 is due to a temporarily unreconciled suspense account.
The increase of $39,000 is mainly explained by the one-time purchase of a specialized laptop.
The increase of $121,000 is explained by an increase in payroll system overpayments which were subsequently resolved.
The Secretariat assisted NSIRA in its work with the departments and agencies subjected to reviews to ensure a timely and unfettered access to all the information necessary for the conduct of reviews. While work remains to be done on this front, we acknowledge the improvements in cooperation and support to the independent review process demonstrated by some reviewees.
There is a risk that the funding received to offset pay increases anticipated over the coming year will be insufficient to cover the costs of such increases and the year-over-year cost of services provided by other government departments/agencies is increasing significantly.
NSIRA Secretariat is closely monitoring pay transactions to identify and address over and under payments in a timely manner and continues to apply ongoing mitigating controls.
Mitigation measures for the risks outlined above have been identified and are factored into NSIRA Secretariat’s approach and timelines for the execution of its mandated activities.
There have been two new Governor-in-Council appointments during the Second quarter, Ms. Colleen Swords and Mr. Jim Chu.
There have been no changes to the NSIRA Secretariat Program.
John Davies
Deputy Head
Marc-André Cloutier
Director General, Corporate Services, Chief Financial Officer
(in thousands of dollars)
| Fiscal year 2023–24 | Fiscal year 2022–23 | |||||
|---|---|---|---|---|---|---|
| Total available for use for the year ending March 31, 2024 (note 1) | Used during the quarter ended September 30, 2023 | Year to date used at quarter-end | Total available for use for the year ending March 31, 2023 (note 1) | Used during the quarter ended September 30, 2022 | Year to date used at quarter-end | |
| Vote 1 – Net operating expenditures | 22,564 | 3,345 | 7,218 | 27,931 | 3,210 | 6,082 |
| Budgetary statutory authorities | ||||||
| Contributions to employee benefit plans | 1,755 | 439 | 878 | 1,728 | 432 | 864 |
| Total budgetary authorities (note 2) | 24,319 | 3,784 | 8,096 | 29,659 | 3,642 | 6,946 |
Note 1: Includes only authorities available for use and granted by Parliament as at quarter-end.
Note 2: Details may not sum to totals due to rounding.
(in thousands of dollars)
| Fiscal year 2023–24 | Fiscal year 2022–23 | |||||
|---|---|---|---|---|---|---|
| Planned expenditures for the year ending March 31, 2024 (note 1) | Expended during the quarter ended September 30, 2023 | Year to date used at quarter-end | Planned expenditures for the year ending March 31, 2023 | Expended during the quarter ended September 30, 2022 | Year to date used at quarter-end | |
| Expenditures | ||||||
| Personnel | 13,303 | 3,014 | 5,900 | 13,245 | 2,903 | 5,248 |
| Transportation and communications | 650 | 62 | 192 | 597 | 70 | 114 |
| Information | 371 | 4 | 4 | 372 | 0 | 5 |
| Professional and special services | 4,906 | 504 | 1,669 | 4,914 | 578 | 1,424 |
| Rentals | 271 | 25 | 73 | 271 | 39 | 49 |
| Repair and maintenance | 4,580 | 24 | 27 | 9,722 | 33 | 64 |
| Utilities, materials and supplies | 73 | 50 | 57 | 173 | 12 | 28 |
| Acquisition of machinery and equipment | 132 | 4 | 52 | 232 | 4 | 13 |
| Other subsidies and payments | 33 | 118 | 122 | 133 | 3 | 1 |
| Total gross budgetary expenditures (note 2) |
24,319 | 3,784 | 8,096 | 29,659 | 3,642 | 6,946 |
Note 1: Includes only authorities available for use and granted by Parliament as at quarter-end.
Note 2: Details may not sum to totals due to rounding.
Date of Publishing:
| CBSA | Canada Border Services Agency |
| CFIA | Canadian Food Inspection Agency |
| CNSC | Canadian Nuclear Safety Commission |
| CRA | Canada Revenue Agency |
| CSE | Communications Security Establishment |
| CSIS | Canadian Security Intelligence Service |
| DND/CAF | Department of National Defence/Canadian Armed Forces |
| FINTRAC | Financial Transactions and Reports Analysis Centre of Canada |
| GAC | Global Affairs Canada |
| GC | Government of Canada |
| IRCC | Immigration, Refugees and Citizenship Canada |
| NSIRA | National Security and Intelligence Review Agency |
| PHAC | Public Health Agency of Canada |
| PS | Public Safety Canada |
| RCMP | Royal Canadian Mounted Police |
| SCIDA | Security of Canada Information Disclosure Act |
| TC | Transport Canada |
| Contribution test | The first part of the two-part threshold that must be met before an institution can make a disclosure under the SCIDA: it must be satisfied that the information will contribute to the exercise of the recipient institution’s jurisdiction or responsibilities in respect of activities that undermine the security of Canada (paragraph 5(1)(a)). |
| Proportionality test | The second part of the two-part threshold that must be met before an institution can make a disclosure under the SCIDA: it must be satisfied that the information will not affect any person’s privacy interest more than reasonably necessary in the circumstances (paragraph 5(1)(b)). |
This review provides an overview of the Security of Canada Information Disclosure Act (SCIDA)’s use in 2022. In doing so, it documents the volume and nature of information disclosures made under the SCIDA; assesses compliance with the SCIDA; and highlights patterns in the SCIDA’s use across Government of Canada (GC) institutions and over time.
In 2022, four disclosing institutions made a total of 173 disclosures to five recipient institutions. The National Security and Intelligence Review Agency (NSIRA) found that institutions complied with the SCIDA’s requirements for disclosure and record keeping in relation to the majority of these disclosures. Instances of non-compliance related to subsection 9(3), regarding the timeliness of records copied to NSIRA; subsection 5.1(1), regarding the timeliness of destruction or return of personal information; and subsection 5(2), regarding the provision of a statement on accuracy and reliability. The observed non-compliance did not point to any systemic failures in GC institutions’ implementation of the SCIDA.
NSIRA also made findings in relation to practices that, although compliant with the SCIDA, left room for improvement. These findings related to:
NSIRA made six recommendations designed to increase standardization across the GC in a manner that is consistent with institutions’ demonstrated best practices and the SCIDA’s guiding principles.
Overall, NSIRA observed improvements in reviewee performance as compared with findings from prior years’ reports and over the course of the review. These improvements include corrective actions taken by reviewees in response to NSIRA’s requests for information in support of this review.
This review was conducted pursuant to paragraph 8(1)(b) and subsection 39(1) of the National Security and Intelligence Review Agency Act (NSIRA Act).
This review provides an overview of the Security of Canada Information Disclosure Act (SCIDA)’s use in 2022. In doing so, it:
The review’s scope was defined by records provided to NSIRA under the SCIDA, subsection 9(3) (see Annex A for a copy of institutions’ section 9 obligations under the Act). As such, the review’s assessment of compliance was limited to the seven GC institutions identified within these records as either disclosers or recipients (Canada Border Services Agency [CBSA], Communications Security Establishment [CSE], Canadian Security Intelligence Service [CSIS], Department of National Defence/Canadian Armed Forces [DND/CAF], Global Affairs Canada [GAC], Immigration, Refugees and Citizenship Canada [IRCC], and the Royal Canadian Mounted Police [RCMP]); and to instances of information disclosure where the SCIDA was identified by these institutions as an authority for disclosure. The review also included Public Safety Canada (PS) in its capacity as manager of the Strategic Coordination Centre on Information Sharing, which provides SCIDA-related policy guidance and training across the GC.
The review satisfies the NSIRA Act’s section 39 requirement for NSIRA to report to the Minister of Public Safety on disclosures made under the SCIDA during the previous calendar year.
The review’s primary source of information was records provided to NSIRA by disclosing and recipient institutions under the SCIDA, subsection 9(3). NSIRA also identified a targeted sample of disclosures for which it requested and assessed all associated documents provided by both the disclosing and recipient institution. This information was supplemented by a document review of institutions’ SCIDA policies and procedures, and related explanations.
NSIRA assessed administrative compliance with the SCIDA’s record-keeping obligations in relation to all disclosures identified in the records provided to NSIRA under subsection 9(3) (N=173). Where these records were incomplete, NSIRA provided an opportunity for institutions to supply the missing records. NSIRA accounted for such late submissions in its assessment of compliance with subsections 9(1) and 9(2).
NSIRA assessed substantive compliance with the SCIDA’s disclosure requirements in relation to the sample of disclosures (n=19). The sample was designed to reflect a non-representative cross-section of the SCIDA’s use, with particular attention to areas at higher risk of non-compliance. Disclosures were selected for the sample based on the content of records provided to NSIRA under subsection 9(3), according to defined parameters (see Annex B, Sample of Disclosures).
NSIRA found that, overall, its expectations for responsiveness by CSE, CSIS, DND/CAF, GAC, IRCC, PS, and RCMP during this review were met. Its expectations for responsiveness by CBSA were partially met, as CBSA required repeated follow-up to provide the requested information.
NSIRA was able to verify information for this review in a manner that met NSIRA’s expectations.
The SCIDA provides an explicit, stand-alone authority to disclose information between GC institutions in order to protect Canada against activities that undermine its security. Its stated purpose is to encourage and facilitate such disclosures.
Section 9 of the SCIDA prescribes record-keeping obligations for all institutions who (1) disclose or (2) receive information under the Act. Each paragraph under subsections 9(1) and 9(2) identifies particular elements that must be set out in the records prepared and kept by each institution (see Annex A). Subsection 9(3) requires that these records be provided to NSIRA within 30 days after the end of each calendar year.
Subsection 5(1) of the SCIDA authorizes GC institutions to disclose information – subject to any prohibitions or restrictions in other legislation or regulations – to designated recipient institutions, if the disclosing institution is satisfied that (a) the information will contribute to the exercise of the recipient institution’s jurisdiction or responsibilities in respect of activities that undermine the security of Canada (the “contribution test”); and (b) the information will not affect any person’s privacy interest more than is reasonably necessary in the circumstances (the “proportionality test”).
Subsection 5(2) requires institutions that disclose information under subsection (1) to, at the time of the disclosure, also provide information regarding its accuracy and the reliability of the manner in which it was obtained.
When a GC institution receives information under the Act, subsection 5.1(1) requires that the institution destroy or return any unnecessary personal information as soon as feasible after receiving it.
The Act’s guiding principles underscore the importance of effectiveness and responsibility across disclosure activities. Of note, subsection 4(c) sets out that information sharing arrangements are appropriate in particular circumstances.
In 2022, four disclosing institutions made a total of 173 disclosures to five recipient institutions (see Table 1). 79% (n=136) of these disclosures were requested by the recipient institution. The other 21% of disclosures (n=37) were sent proactively by the disclosing institution.
| Designated Recipient Institutions | ||||||||||||||||||
| Disclosing Institution | CBSA | CFIA | CNSC | CRA | CSE | CSIS | DND/CAF | Finance | FINTRAC | GAC | Health | IRCC | PHAC | PSC | RCMP | TC | TOTAL (proactive) | |
| CBSA | – | – | – | – | – | – | – | – | – | – | – | – | – | – | 4 (3) |
– | 4 (3) |
|
| GAC | – | – | – | – | – | 39 (18) |
2 (2) |
– | – | – | – | – | – | – | 12 (12) |
– | 53 (32) |
|
| IRCC | – | – | – | – | 59 (0) |
56 (2) |
– | – | – | – | – | – | – | – | – | – | 115 (2) |
|
| RCMP | – | – | – | – | – | – | – | – | – | – | – | 1 (0) |
– | – | – | – | 1 (0) |
|
| TOTAL (proactive) | – | – | – | – | 59 (0) |
95 (20) |
2 (2) |
– | – | – | – | 1 (0) |
– | – | 16 (15) |
– | 173 (37) |
|
The total number of disclosures made under the SCIDA since its implementation reflects a slight downward trend, with a generally constant proportion of requested versus proactive disclosures for the years in which this data was collected (see Figure 1).

In 2022, these disclosures were made and received by institutions that had each disclosed or received information, as the case may be, in at least two prior review years (see Annex C, Overview of SCIDA Disclosures in Prior Years).
Finding 1: NSIRA found that CSE, CSIS, GAC, and IRCC regularly use the SCIDA in a manner that warrants information sharing arrangements, as encouraged by subsection 4(c) of the SCIDA.
CSE, CSIS, GAC, and IRCC were the most frequent users of the SCIDA in 2022. The number of disclosures between these institutions was comparable to those observed by NSIRA in prior years (see Annex C), indicating the occurrence of regular exchange over time.
NSIRA also observed regular patterns in the purpose and nature of the information exchanged between these institutions in 2022, as described in Table 2. These information exchanges were not governed by up-to-date information sharing arrangements.
| GAC-to-CSIS (N=39) | IRCC-to-CSIS (N=56) | IRCC-to-CSE (N=59) |
|---|---|---|
|
|
|
NSIRA has previously recommended that information sharing arrangements be updated (for GAC and CSIS) or created (for IRCC and CSE) to govern certain information exchanges made under the SCIDA.
Recommendation 1: NSIRA recommends that information sharing arrangements be used to govern regular SCIDA disclosures between GAC and CSIS; IRCC and CSIS; as well as IRCC and CSE.
Finding 2: NSIRA found that CBSA, DND/CAF, and IRCC were non-compliant with subsection 9(3) of the SCIDA, as they failed to provide all records created under subsections 9(1) or 9(2) to NSIRA within the legislated timeframe.
Requests for information from NSIRA during the course of this review prompted the late production of additional records relating to paragraphs under subsections 9(1) or 9(2) from each of CBSA, DND/CAF, and IRCC (see Table 3).
| Administrative Error | Delayed Preparation of Records | |
|---|---|---|
| CBSA | 2 [paragraph 9(1)(e)] | – |
| DND/CAF | – | 2 [paragraphs 9(2)(e-g)] |
| IRCC | 6 [paragraph 9(1)(e)] | 1 [paragraphs 9(2)(e-g)] |
CBSA and IRCC were non-compliant with subsection 9(3) due to administrative error; the records they eventually supplied had existed at the time of the reporting deadline, but were not copied to NSIRA as required.
NSIRA expected that all records would be prepared within 30 days after the end of the calendar year, in order to meet the subsection 9(3) requirement to provide a copy of those records to NSIRA within that timeframe.
DND/CAF and IRCC were non-compliant with subsection 9(3) on account of delayed preparation of records; they did not prepare the records referred to in Table 3 within 30 days after the end of the calendar year, and therefore did not provide a copy of them to NSIRA within the legislated timeframe.
NSIRA underscores the importance of administrative precision and timeliness in preparing records and copying them to NSIRA.
Finding 3: NSIRA found improved compliance outcomes in instances where departments prepared record overview spreadsheets under subsections 9(1) and 9(2) of the SCIDA that displayed the following characteristics:
The SCIDA does not specify a format for records prepared under section 9. Accordingly, in 2022, GC institutions fulfilled their record-keeping obligations in different ways.
Most institutions provided NSIRA with an overview of each disclosure made or received. These overviews were submitted to NSIRA as spreadsheets that generally captured the information required in records under subsections 9(1) and 9(2).
Most institutions also provided NSIRA with a copy of the disclosure itself and a selection of related documents. These documents often included email consultations with legal services, disclosure request letters, and other correspondence between disclosing and recipient institutions. The scope of requests for information in the course of the review was minimized in cases where institutions provided such documents.
DND/CAF and IRCC (for its one disclosure receipt) were the only institutions that originally provided NSIRA with a copy of the raw disclosure, including transmittal details, in the absence of a record overview or other related documents.
NSIRA observed that DND/CAF and IRCC’s choice in records format for these disclosures contributed to their non-compliance with subsection 9(3), described in Table 3. The information elicited under paragraphs 9(2)(e-g) cannot by definition be found within a copy of the disclosure itself, as it relates to action taken by recipient institutions following the disclosure’s receipt. A copy of the disclosure on its own is therefore insufficient to comply with all requirements under subsection 9(2).
Both DND/CAF and IRCC were infrequent recipients of disclosures under the SCIDA in 2022, accounting for only two and one disclosures, respectively. Each of the more frequent recipients of information (CSE, CSIS, and RCMP) included express columns in their record overview spreadsheets to capture whether and, if applicable, when personal information was destroyed or returned, per the requirements of paragraphs 9(2)(e-g).
NSIRA also observed that CBSA and IRCC’s choice in records format contributed to their non-compliance with subsection 9(3) due to administrative error. These institutions did not account for the full scope of information required under paragraph 9(1)(e) in their record overview spreadsheets.
The information relied upon to satisfy the disclosing institution that a disclosure is authorized under the Act is not required to be conveyed within the disclosure itself. Completing an appropriately-specified record overview spreadsheet is therefore an effective way to ensure that the corresponding information is documented and conveyed to NSIRA ahead of the legislated deadline.
The RCMP’s record overview spreadsheet was particularly effective in demonstrating compliance with the Act. The spreadsheet included columns that were explicitly tied to individual paragraphs under section 9, with additional fields limited to RCMP administrative information such as file and database reference numbers.
Spreadsheets designed in this way enable institutions’ efficient self-assessment against the requirements of the Act. They also facilitate the task of review by clearly matching the information provided with its corresponding requirement under the SCIDA, and by organizing disclosures and receipts of information in a manner that supports cross-verification.
Recommendation 2: NSIRA recommends that all GC institutions prepare record overviews to clearly address the requirements of subsections 9(1) and 9(2) of the SCIDA; and provide them to NSIRA along with a copy of the disclosure itself and, where relevant, a copy of the request.
Finding 4: NSIRA found that all GC institutions complied with their obligation to prepare and keep records that set out the information prescribed under subsections 9(1) and 9(2) of the SCIDA.
Finding 5: NSIRA found that more than half of the descriptions provided by CBSA and IRCC under paragraph 9(1)(e) of the SCIDA did not explicitly address their satisfaction that the disclosure was authorized under paragraph 5(1)(b), the proportionality test.
Although NSIRA expected an express statement describing the information that was relied on to satisfy the disclosing institution that the disclosure was authorized under the SCIDA, in this review, NSIRA considered any records that demonstrated the corresponding assessment had been conducted.
IRCC n’a pas fait de déclaration expresse précisant que les communications demandées par le SCRS, qui représentent 57 % (n=54) de l’ensemble de ses communications, lui semblaient satisfaisantes du point de vue du critère de proportionnalité. En revanche, IRCC a fourni des copies des lettres de demande et de l’information communiquée en guise de réponse, ce qui confirme que la communication était manifestement conforme aux besoins précis de la demande (et donc témoigne d’une évaluation de la proportionnalité).
L’ASFC n’a pas fourni de déclaration expresse concernant sa satisfaction au regard du critère de proportionnalité pour 75 % (n=3) de ses communications. Elle a plutôt démontré qu’elle tenait compte du principe de proportionnalité en fournissant divers documents justificatifs, y compris de la correspondance interne.
La feuille de calcul utilisée par AMC pour donner une vue d’ensemble de ses documents a été particulièrement efficace pour répondre aux exigences de l’alinéa 9(1)e). L’analyse détaillée qu’elle a consignée en ce qui concerne les critères de contribution et de proportionnalité lui a permis de remplir ses obligations en matière de conservation des dossiers et de démontrer qu’elle respectait en substance le paragraphe 5(1).
Recommendation 3: NSIRA recommends that disclosing institutions explicitly address the requirements of both paragraphs 5(1)(a) and 5(1)(b) in the records that they prepare under paragraph 9(1)(e) of the SCIDA.
Finding 6: NSIRA found, within the sample of disclosures reviewed, that disclosing institutions demonstrated they had satisfied themselves of both the contribution and proportionality tests, in compliance with subsection 5(1) of the SCIDA.
Finding 7: NSIRA found that GAC satisfied itself under the SCIDA’s paragraph 5(1)(a) contribution test based on an incorrect understanding of the recipient’s national security mandate in two cases.
The threshold for compliance with subsection 5(1) is that the disclosing institution has satisfied itself of the contribution and proportionality tests, and that it has done so prior to having made the disclosure.
In relation to the two disclosures that it made proactively to DND/CAF, GAC provided a rationale for the information’s contribution to DND/CAF’s mandate in respect of national security. Upon receipt of the information, however, DND/CAF did not agree with GAC’s assessment and therefore assessed that the SCIDA was not an appropriate disclosure mechanism in the circumstances.
Informal communication between the two institutions may have allowed DND/CAF and GAC to resolve this issue prior to the disclosure. When such communications occur, it is important that they be limited to the information necessary to confirm that the information contributes to the recipient’s mandate in respect of activities that undermine the security of Canada.
Recommendation 4: NSIRA recommends that GC institutions contemplating the use of proactive disclosures under the SCIDA communicate with the recipient institution, ahead of making the disclosure, to inform their assessments under subsection 5(1).
Finding 8: NSIRA found, within the sample of disclosures reviewed, that CBSA and GAC (in one and two disclosures, respectively) were non-compliant with the SCIDA’s subsection 5(2) requirement to provide a statement regarding accuracy and reliability.
Finding 9: NSIRA found, in relation to the remaining disclosures within the sample, that GAC, IRCC, and RCMP included their statements regarding accuracy and reliability within the disclosures themselves, whereas CBSA provided its statements in the disclosures’ cover letters.
Providing the statement on accuracy and reliability in a cover letter for the disclosure satisfies the Act’s requirement to provide the statement at the time of disclosure. However, separating the statement from the information disclosed increases the risk that the information may be subsequently used without awareness of relevant qualifiers. The location of the statement on accuracy and reliability – and not just its contemporaneous provision to the recipient – is therefore relevant to its value added.
Recommendation 5: NSIRA recommends that all disclosing institutions include statements regarding accuracy and reliability within the same document as the disclosed information.
Finding 10: NSIRA found that DND/CAF destroyed information under the SCIDA subsection 5.1(1), but they were non-compliant with the requirement to do so “as soon as feasible after receiving it.”
DND/CAF determined, upon receipt of the two disclosures it received from GAC, that the personal information contained within the disclosures should not be retained. The information, however, was not destroyed until April 2023 – 12 days following a request for information from NSIRA to provide a copy of records that set out whether and when the information had been destroyed or returned. The date of destruction was 299 and 336 days following DND/CAF’s receipt of each disclosure.
Taking into consideration the elapsed time between receipt of the information and its destruction, as well as DND/CAF’s timely conclusion that the information should not be retained, DND/CAF’s ultimate destruction of the information was non-compliant with the requirement to destroy the information “as soon as feasible after receiving it.” Its delay in this respect was also inconsistent with the responsible use and management of the information.
DND/CAF was the only institution to identify any disclosures as containing information that was destroyed or returned under subsection 5.1(1) in 2022. NSIRA did not identify any other disclosures within the sample for which personal information disclosed should have been destroyed or returned.
Finding 11: NSIRA found delays between when a disclosure was authorized for sending and when it was received by the individual designated by the head of the recipient institution to receive it in at least 20% (n=34) of disclosures.
These 34 disclosures include 29 for which there was a delay between the dates provided by disclosing and recipient institutions in their section 9 records, as well as an additional five for which CSIS reported both the date of administrative receipt within the institution and the subsequent date of receipt by the person designated by the head to receive it (i.e., the relevant operational unit).
NSIRA attributes most of these delays to expected dynamics in classified information sharing: the individual authorizing the disclosure is not always the same individual who administratively sends it to the recipient, and the person who administratively receives the disclosure is not always the same person who is designated by the head to receive it.
In the majority of cases, the observed delays were shorter than one week. In nine cases, however, the delay ranged from 30 to 233 days.
Such delays mean that information is not processed and actioned within the recipient institution until long after it was sent – or intended to be sent – by the individual authorizing the disclosure. While these delays do not amount to non-compliance with the SCIDA, they are inconsistent with the Act’s purpose and guiding principles.
Recommendation 6: NSIRA recommends that GC institutions review their administrative processes for sending and receiving disclosures under the SCIDA, and correct practices that cause delays.
The SCIDA’s requirements for disclosure and record keeping apply to both disclosing and recipient institutions in all cases where the SCIDA is invoked as a mechanism for disclosure. This review assessed GC institutions’ compliance with requirements for record keeping in respect of all 173 disclosures that were made and received in 2022. It assessed their compliance with requirements for disclosure in relation to a targeted sample of 19 disclosures.
NSIRA found that institutions complied with the SCIDA’s requirements for disclosure and record keeping in relation to the majority of disclosures. GC institutions’ non-compliance with subsection 9(3) was driven by irregularities in the reporting of 11 disclosures. Observed non-compliance with substantive requirements under subsection 5(2) related to three disclosures; and non-compliance with subsection 5.1(1) related to two disclosures. These instances of non-compliance do not point to any systemic failures in GC institutions’ implementation of the SCIDA.
Within this context, NSIRA observed improvements in reviewee performance as compared with findings from prior years’ reports and over the course of the review. Of note, NSIRA’s requests for information in support of this review prompted corrective action by CBSA, DND/CAF, and IRCC that would have otherwise amounted to non-compliance with requirements under section 9.
NSIRA also observed several practices that, although compliant with the SCIDA, leave room for improvement. NSIRA’s recommendations in this review are designed to increase standardization across the GC in a manner that is consistent with institutions’ demonstrated best practices and the SCIDA’s guiding principles.
| Obligation – disclosing institution | Obligation — recipient institution |
|---|---|
| 9 (1) Every Government of Canada institution that discloses information under this Act must prepare and keep records that set out | (2) Every Government of Canada institution that receives information under this Act must prepare and keep records that set out |
| (a) a description of the information; | (a) a description of the information; |
| (b) the name of the individual who authorized its disclosure; | (b) the name of the institution that disclosed it; |
| (c) the name of the recipient Government of Canada institution; | (c) the name or position of the head of the recipient institution — or of the person designated by the head — who received the information; |
| (d) the date on which it was disclosed; | (d) the date on which it was received by the recipient institution; |
| (e) a description of the information that was relied on to satisfy the disclosing institution that the disclosure was authorized under this Act; and |
(e) whether the information has been destroyed or returned under subsection 5.1(1); (f) if the information has been destroyed under subsection 5.1(1), the date on which it was destroyed; (g) if the information was returned under subsection 5.1(1) to the institution that disclosed it, the date on which it was returned; and |
| (f) any other information specified by the regulations. | (h) any other information specified by the regulations. |
Within 30 days after the end of each calendar year, every Government of Canada institution that disclosed information under section 5 during the year and every Government of Canada institution that received such information must provide the National Security and Intelligence Review Agency with a copy of every record it prepared under subsection (1) or (2), as the case may be, with respect to the information.
Disclosures were selected for the sample based on the content of records provided to NSIRA under subsection 9(3), according to the following parameters:
Drawing on information published in previous NSIRA reports, Table 5 summarizes the number and distribution of disclosures made under the SCIDA in prior years.
| Designated Recipient Institutions | ||||||||||||||||||
| Disclosing Institution | CBSA | CFIA | CNSC | CRA | CSE | CSIS | DND/CAF | Finance | FINTRAC | GAC | Health | IRCC | PHAC | PSC | RCMP | TC | TOTAL (proactive) | |
| 2021 | DND/CAF | – | – | – | – | – | 2 | – | – | – | – | – | – | – | – | – | – | 2 |
| GAC | – | – | – | – | – | 41 | – | – | – | – | – | 1 | – | – | 2 | – | 44 | |
| IRCC | – | – | – | – | 68 | 79 | – | – | – | 2 | – | – | – | – | – | – | 149 | |
| TOTAL | – | – | – | – | 68 | 122 | – | – | – | 2 | – | 1 | – | – | 2 | – | 195 | |
| 2020 | CBSA | – | – | – | – | – | 1 | – | – | – | – | – | – | – | – | 3 | – | 4 |
| GAC | – | – | – | – | 1 | 25 | – | – | – | – | – | 1 | – | – | 13 | – | 40 | |
| IRCC | – | – | – | – | 60 | 61 | – | – | – | – | – | – | – | – | 37 | 1 | 159 | |
| RCMP | – | – | – | – | – | – | 1 | – | – | 3 | – | 5 | – | – | – | – | 9 | |
| TC | – | – | – | – | – | – | – | – | – | – | – | – | – | – | 2 | – | 2 | |
| Other | – | – | – | – | – | 1 | – | – | – | – | – | – | – | – | – | – | 1 | |
| TOTAL | – | – | – | – | 61 | 88 | 1 | – | – | 3 | – | 6 | – | – | 55 | 1 | 215 | |
| 2019 | CBSA | – | – | – | – | – | 1 | – | – | – | – | – | – | – | – | 2 | – | 3 |
| GAC | – | – | – | – | – | 23 | – | – | – | – | – | 3 | – | 1 | 15 | – | 42 | |
| IRCC | – | – | – | – | 5 | 17 | 1 | – | – | – | – | – | – | – | 36 | – | 59 | |
| RCMP | – | – | – | 4 | – | – | – | – | 1 | 3 | – | 1 | – | – | – | – | 9 | |
| TC | – | – | – | – | – | – | – | – | – | – | – | – | – | – | 1 | – | 1 | |
| TOTAL | – | – | – | 4 | 5 | 41 | 1 | – | 1 | 3 | – | 4 | – | 1 | 54 | – | 114 | |
NSIRA found that CSE, CSIS, GAC, and IRCC regularly use the SCIDA in a manner that warrants information sharing arrangements, as encouraged by subsection 4(c) of the SCIDA.
NSIRA found that CBSA, DND/CAF, and IRCC were non-compliant with subsection 9(3) of the SCIDA, as they failed to provide all records created under subsections 9(1) or 9(2) to NSIRA within the legislated timeframe.
NSIRA found improved compliance outcomes in instances where departments prepared record overview spreadsheets under subsections 9(1) and 9(2) of the SCIDA that displayed the following characteristics:
NSIRA found that all GC institutions complied with their obligation to prepare and keep records that set out the information prescribed under subsections 9(1) and 9(2) of the SCIDA.
NSIRA found that more than half of the descriptions provided by CBSA and IRCC under paragraph 9(1)(e) of the SCIDA did not explicitly address their satisfaction that the disclosure was authorized under paragraph 5(1)(b), the proportionality test.
NSIRA found, within the sample of disclosures reviewed, that disclosing institutions demonstrated they had satisfied themselves of both the contribution and proportionality tests, in compliance with subsection 5(1) of the SCIDA.
NSIRA found that GAC satisfied itself under the SCIDA’s paragraph 5(1)(a) contribution test based on an incorrect understanding of the recipient’s national security mandate in two cases.
NSIRA found, within the sample of disclosures reviewed, that CBSA and GAC (in one and two disclosures, respectively) were non-compliant with the SCIDA’s subsection 5(2) requirement to provide a statement regarding accuracy and reliability.
NSIRA found, in relation to the remaining disclosures within the sample, that GAC, IRCC, and RCMP included their statements regarding accuracy and reliability within the disclosures themselves, whereas CBSA provided its statements in the disclosures’ cover letters.
NSIRA found that DND/CAF destroyed information under the SCIDA subsection 5.1(1), but they were non-compliant with the requirement to do so “as soon as feasible after receiving it.”
NSIRA found delays between when a disclosure was authorized for sending and when it was received by the individual designated by the head of the recipient institution to receive it in at least 20% (n=34) of disclosures.
Last Updated:
Status:
Published
Review Number:
23-03
Date of Publishing:
This quarterly report has been prepared by management as required by section 65.1 of the Financial Administration Act and in the form and manner prescribed by the Directive on Accounting Standards, GC 4400 Departmental Quarterly Financial Report. This quarterly financial report should be read in conjunction with the 2023–24 Main Estimates.
This quarterly report has not been subject to an external audit or review.
The National Security and Intelligence Review Agency (NSIRA) is an independent external review body that reports to Parliament. Established in July 2019, NSIRA is responsible for conducting reviews of the Government of Canada’s national security and intelligence activities to ensure that they are lawful, reasonable and necessary. NSIRA also hears public complaints regarding key national security agencies and their activities.
A summary description NSIRA’s program activities can be found in Part II of the Main Estimates. Information on NSIRA’s mandate can be found on its website.
This quarterly report has been prepared by management using an expenditure basis of accounting. The accompanying Statement of Authorities includes the agency’s spending authorities granted by Parliament and those used by the agency, consistent with the 2023–24 Main Estimates. This quarterly report has been prepared using a special-purpose financial reporting framework (cash basis) designed to meet financial information needs with respect to the use of spending authorities.
The authority of Parliament is required before money can be spent by the government. Approvals are given in the form of annually approved limits through appropriation acts or through legislation in the form of statutory spending authorities for specific purposes.
This section highlights the significant items that contributed to the net increase or decrease in authorities available for the year and actual expenditures for the quarter ended June 30, 2023.
NSIRA spent approximately 19% of its authorities by the end of the first quarter, compared with 12% in the same quarter of 2022–23 (see graph 1).
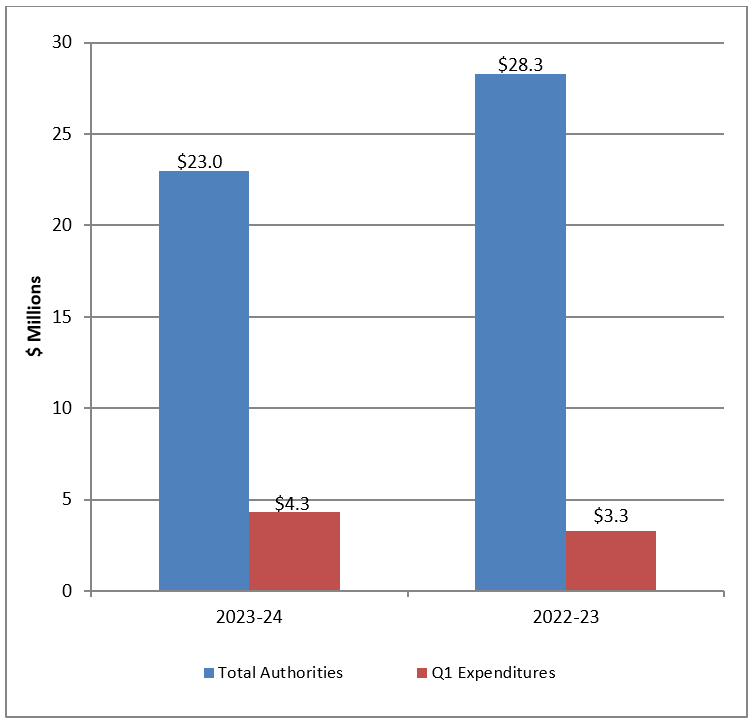
| 2023-24 | 2022-23 | |
|---|---|---|
| Total Authorities | $23.0 | $28.3 |
| Q1 Expenditures | $4.3 | $3.3 |
As of June 30, 2023, Parliament had approved $23.0 million in total authorities for use by NSIRA for 2023–24 compared with $28.3 million as of June 30th, 2022, for a net decrease of $5.3 million or 8.1% (see graph 2).
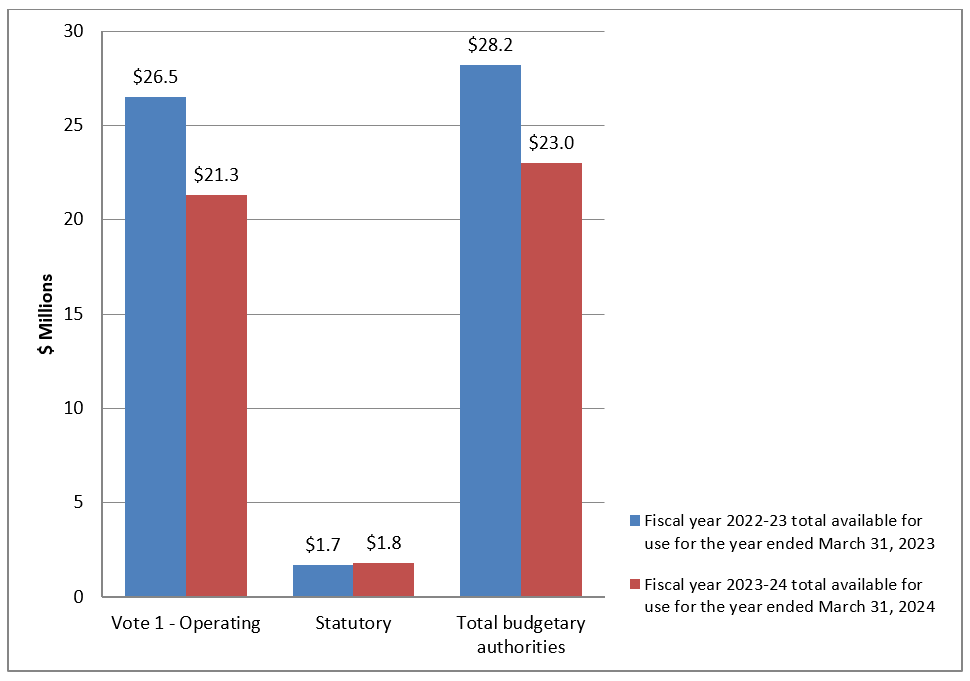
| Fiscal year 2022-23 total available for use for the year ended March 31, 2023 | Fiscal year 2023-24 total available for use for the year ended March 31, 2024 | |
|---|---|---|
| Vote 1 – Operating | 26.5 | 21.3 |
| Statutory | 1.7 | 1.8 |
| Total budgetary authorities | 28.2 | 23.0 |
*Details may not sum to totals due to rounding*
The decrease of $5.3 million in authorities is mostly explained by a reduction in capital funding for infrastructure projects.
The first quarter expenditures totalled $4.3 million for an increase of $1 million when compared with $3.3 million spent during the same period in 2022–23. Table 1 presents budgetary expenditures by standard object.
| Variances in expenditures by standard object(in thousands of dollars) | Fiscal year 2023–24: expended during the quarter ended June 30, 2023 | Fiscal year 2022–23: expended during the quarter ended June 30, 2022 | Variance $ | Variance % |
|---|---|---|---|---|
| Personnel | 2,886 | 2,345 | 541 | 23% |
| Transportation and communications | 130 | 44 | 86 | 195% |
| Information | 0 | 5 | (5) | 100% |
| Professional and special services | 1,165 | 846 | 319 | 38% |
| Rentals | 48 | 10 | 38 | 380% |
| Repair and maintenance | 24 | 31 | (7) | (23%) |
| Utilities, materials and supplies | 7 | 16 | (9) | (56%)% |
| Acquisition of machinery and equipment | 48 | 9 | 39 | 433% |
| Other subsidies and payment | 4 | (2) | (6) | (300%) |
| Total gross budgetary expenditures | 4,312 | 3,304 | 1,008 | 31% |
The increase of $541,000 is largely caused by an increase in cost per FTE and change in the timing of Member’s pay.
The increase of $86,000 is explained by a change in the timing of invoicing for the internet connection.
The increase of $319,000 is mainly explained by an increase in the cost of the maintenance and services in support of our classified IT network infrastructure. It also relates to the use of guard services for office accommodation fit-up.
The increase of $38,000 is explained by a change in the timing of invoicing for the rent for temporary office space.
The increase of $39,000 is explained by a one-time purchase of a specialized laptop along with a wall mounted charging station and warranty.
The Secretariat assisted NSIRA in its work with the departments and agencies subjected to reviews to ensure a timely and unfettered access to all the information necessary for the conduct of reviews. While work remains to be done on this front, we acknowledge the improvements in cooperation and support to the independent review process demonstrated by some reviewees.
There is a risk that the funding received to offset pay increases anticipated over the coming year will be insufficient to cover the costs of such increases and the year-over-year cost of services provided by other government departments/agencies is increasing significantly.
NSIRA is closely monitoring pay transactions to identify and address over and under payments in a timely manner and continues to apply ongoing mitigating controls.
Mitigation measures for the risks outlined above have been identified and are factored into NSIRA’s approach and timelines for the execution of its mandated activities.
There have been no new Governor-in-Council appointments during the first quarter.
Mr. Pierre Souligny, NSIRA’s Senior Director, Corporate Services and CFO since 2020, has retired. He has been replaced by Mr. Marc-André Cloutier.
John Davies
Deputy Head
Pierre Souligny
Chief Financial Officer
(in thousands of dollars)
| Fiscal year 2023–24 | Fiscal year 2022–23 | |||||
|---|---|---|---|---|---|---|
| Total available for use for the year ending March 31, 2024 (note 1) | Used during the quarter ended June 30, 2023 | Year to date used at quarter-end | Total available for use for the year ending March 31, 2023 (note 1) | Used during the quarter ended June 30, 2022 | Year to date used at quarter-end | |
| Vote 1 – Net operating expenditures | 21,254 | 3,873 | 3,873 | 26,523 | 2,872 | 2,872 |
| Budgetary statutory authorities | ||||||
| Contributions to employee benefit plans | 1,728 | 439 | 439 | 1,728 | 432 | 432 |
| Total budgetary authorities (note 2) | 23,009 | 4,312 | 4,312 | 28,251 | 3,304 | 3,304 |
Note 1: Includes only authorities available for use and granted by Parliament as at quarter-end.
Note 2: Details may not sum to totals due to rounding.
(in thousands of dollars)
| Fiscal year 2023–24 | Fiscal year 2022–23 | |||||
|---|---|---|---|---|---|---|
| Planned expenditures for the year ending March 31, 2024 (note 1) | Expended during the quarter ended June 30, 2023 | Year to date used at quarter-end | Planned expenditures for the year ending March 31, 2023 | Expended during the quarter ended June 30, 2022 | Year to date used at quarter-end | |
| Expenditures | ||||||
| Personnel | 13,303 | 2,886 | 2,886 | 13,245 | 2,345 | 2,345 |
| Transportation and communications | 650 | 130 | 130 | 597 | 44 | 44 |
| Information | 372 | 0 | 0 | 372 | 5 | 5 |
| Professional and special services | 3,596 | 1,165 | 1,165 | 3,506 | 846 | 846 |
| Rentals | 271 | 48 | 48 | 271 | 10 | 10 |
| Repair and maintenance | 4,580 | 24 | 24 | 9,722 | 31 | 31 |
| Utilities, materials and supplies | 73 | 7 | 7 | 103 | 3 | 3 |
| Acquisition of machinery and equipment | 132 | 48 | 48 | 232 | 9 | 9 |
| Other subsidies and payments | 33 | 4 | 4 | 133 | (2) | (2) |
| Total gross budgetary expenditures (note 2) |
23,009 | 4,312 | 4,312 | 28,251 | 3,304 | 3,304 |
Note 1: Includes only authorities available for use and granted by Parliament as at quarter-end.
Note 2: Details may not sum to totals due to rounding.