- Executive Summary
- Authorities
- Introduction
- Background
- Findings and recommendations
- Conclusion
- Annexes
- ANNEX A: Objectives, Scope, and Methodology
- ANNEX B: Meetings and Briefings
- ANNEX C: Findings and Recommendations
- ANNEX D: Partner and client information and publicly available information shared between the fi and cybersecurity aspects
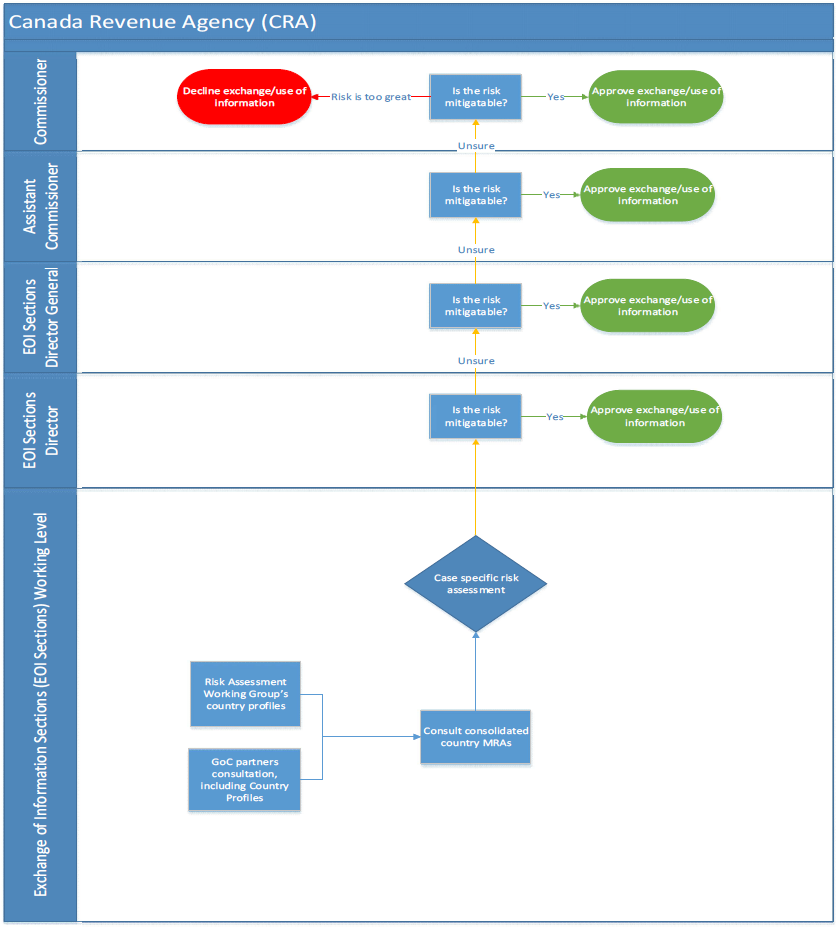
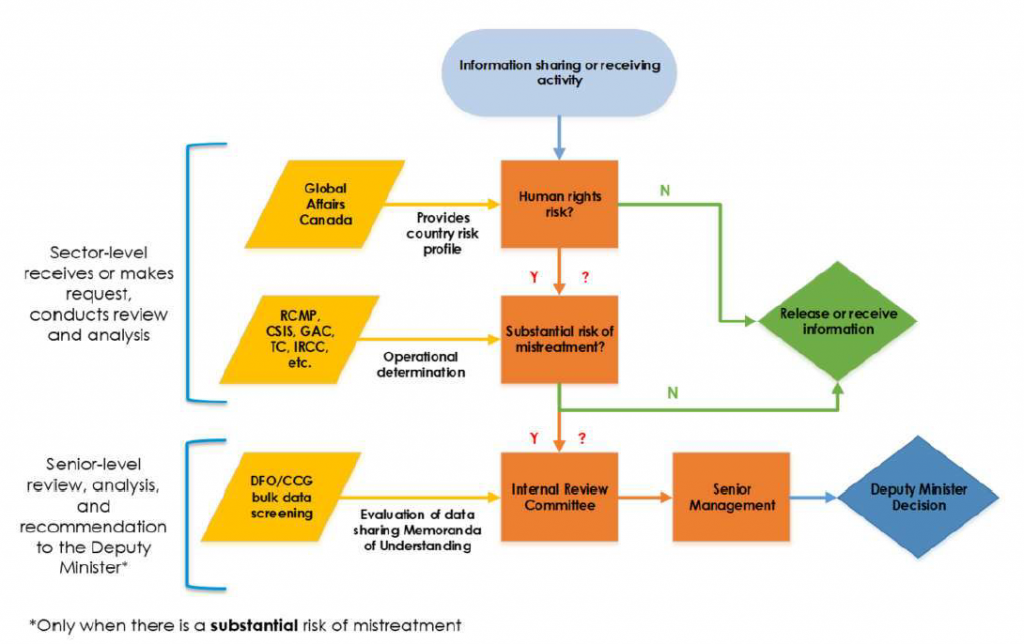
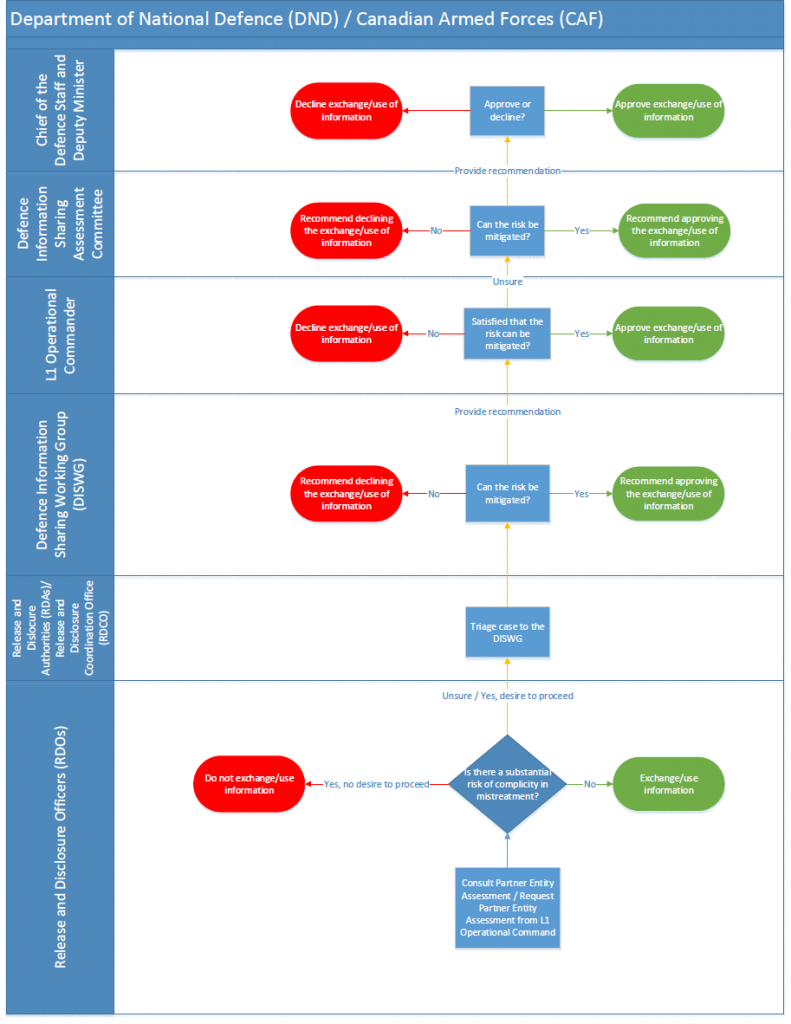
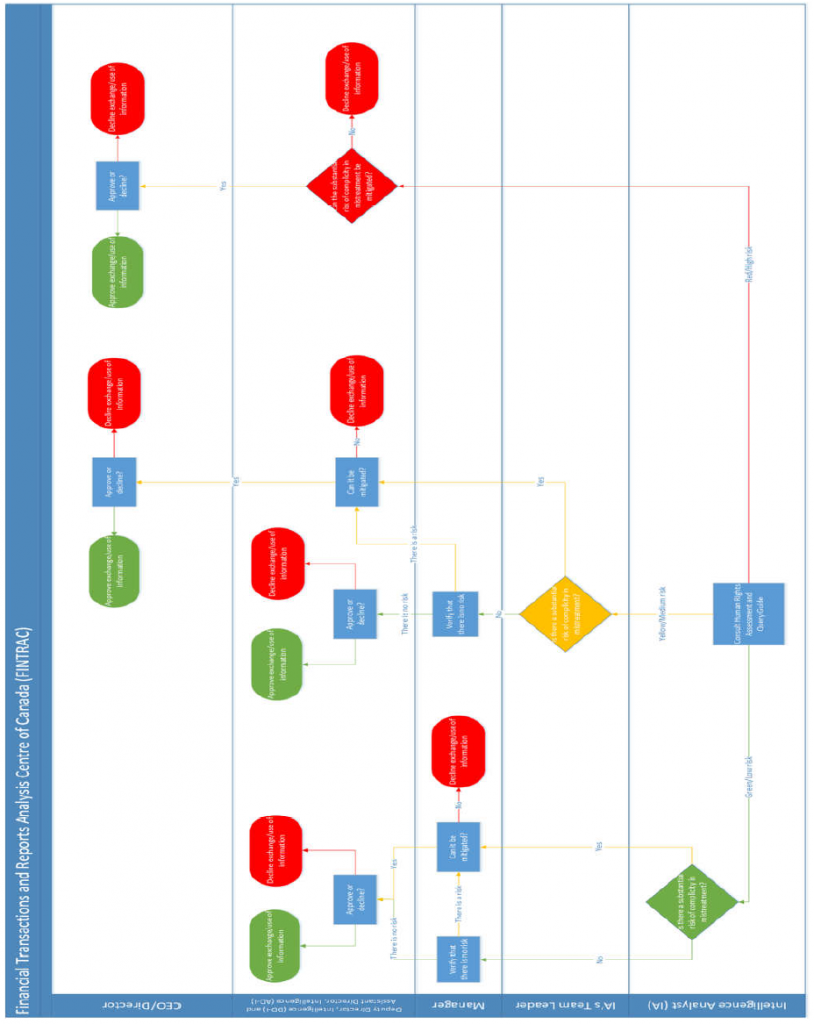
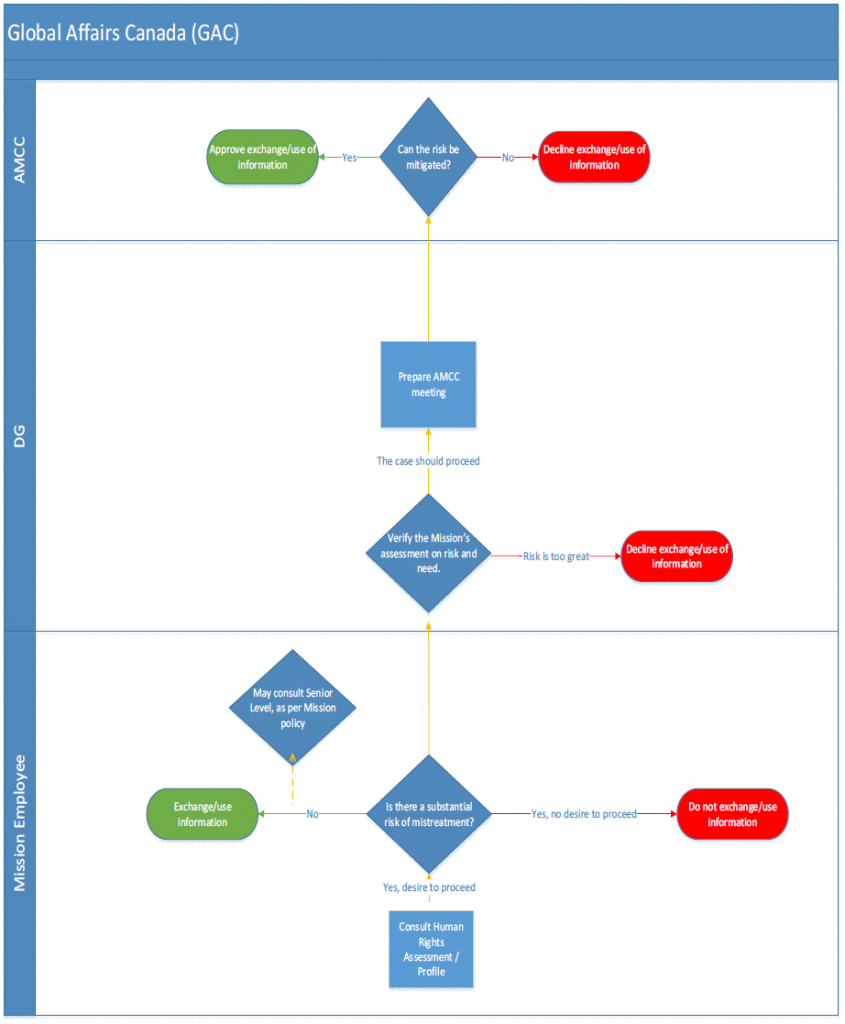
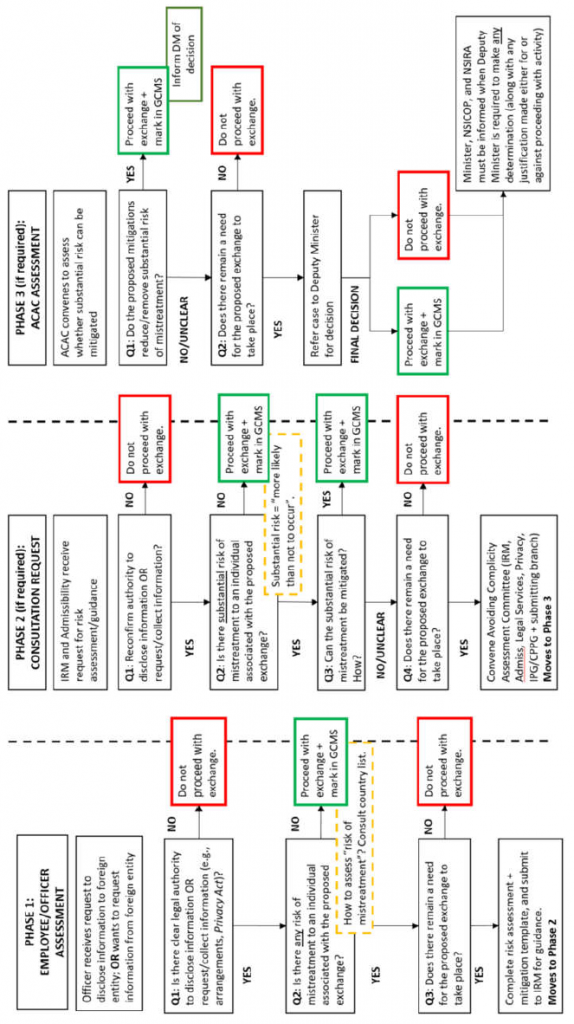
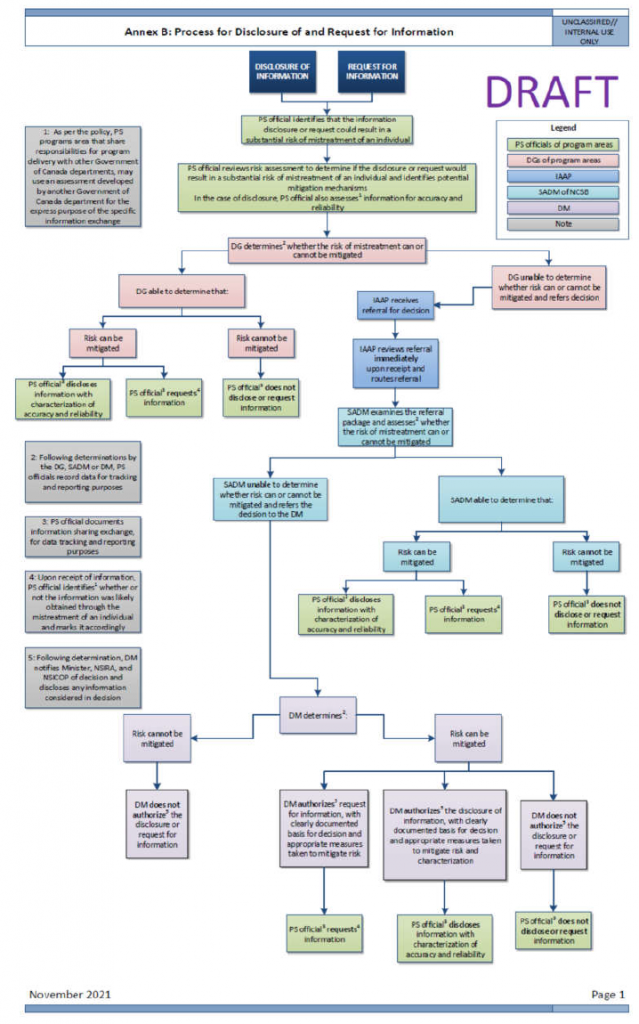
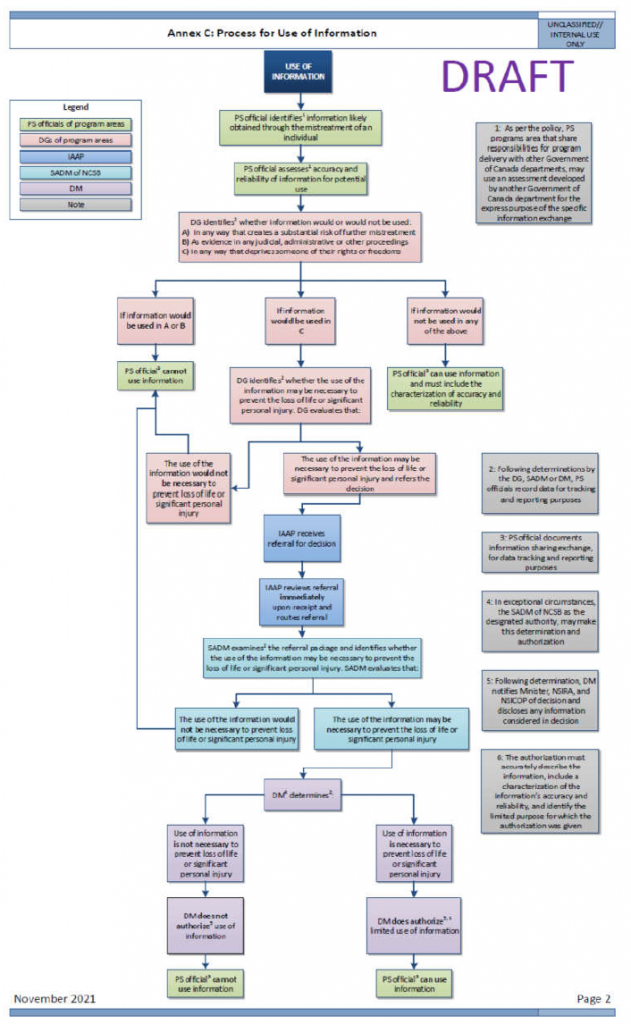
- ANNEX E: Approval Process and Sharing Release Approvals
- ANNEX F: Methods and processes of sharing
- ANNEX G: Policy Thresholds for Internal Sharing
- ANNEX H: Internal Sharing of IRTC at CSE
Date of Publishing:
GAC Minister letter to NSIRA To Follow
This report has been modified slightly from the final version which was provided to the Minister. An error in the language of Finding 4, wherein two different versions were presented within the report and the summary, has been corrected for publication. The correct language was always represented in the body of the final report. The incorrect language has been replaced with the correct language for publication.
Executive Summary
(U) This review examined the Communications Security Establishment’s (CSE) legal authority for sharing information obtained in the course of one aspect of its mandate (“aspect”) for the purposes of fulfilling another aspect of its mandate. Specifically, the review focused on internal information sharing within CSE between the foreign intelligence (FI), and the cybersecurity and information assurance (cybersecurity) aspects of its mandate.
(U) NSIRA examined whether CSE’s internal sharing of information relating to a Canadian or a person in Canada (IRTC) is consistent with the Privacy Act, which limits how collected personal information can be used by a federal institution, and the CSE Act, which applies to CSE’s incidental collection and use of IRTC. NSIRA concluded that from the descriptions of the aspects in sections 16 and 17 of the CSE Act, there may be instances where information acquired under one aspect can be used for the same, or a consistent purpose, as another. This would satisfy Privacy Act requirements for sharing information internally. However, this cannot simply be assumed as the purposes of the aspects differ within the CSE Act. CSE must conduct case-by- case compliance analysis that considers the purpose of the collection and sharing.
(U) NSIRA considers it necessary for the Chief of CSE’s application for a Ministerial Authorization to fully inform the Minister of how IRTC might be used and analysed by CSE, including the sharing of IRTC to another aspect, and for what purpose. With one exception, the Chief’s applications for the period of review appropriately informed the Minister of National Defence that retained IRTC might be used to support a different aspect. Moreover, the foreign intelligence applications appropriately informed the Minister how CSE assessed “essentiality” for IRTC collected under the FI aspect.
(U) Under CSE policy, an assessment of IRTC’s relevance, essentiality, or necessity to each aspect is required for sharing information across the aspects. CSE policy offers definitions and criteria for assessing and applying these thresholds to the information. NSIRA found that CSE’s policy framework with regards to the internal sharing of information between the foreign intelligence and cybersecurity aspects of the mandate is compliant with the CSE Act.
(U) The information provided by CSE has not been independently verified by NSIRA. Work is underway to establish effective policies and best practices for the independent verification of various kinds of information, in keeping with NSIRA’s commitment to a ‘trust but verify’ approach.
Authorities
(U) This review was conducted under the authority of paragraph 8(1)(a) of the National Security and Intelligence Review Agency Act (NSIRA Act).
Introduction
(U) This review examined the Communications Security Establishment’s (CSE) legal authority for sharing information obtained in the course of one aspect of its mandate (“aspect”) for the purposes of fulfilling another aspect of its mandate. Specifically, the review focused on internal information sharing within CSE between the foreign intelligence (FI), and the cybersecurity and information assurance (cybersecurity) aspects of its mandate. Broadly, this review also documented activities pertaining to the internal sharing of information relating to a Canadian or a person in Canada between the foreign intelligence and cybersecurity aspects, in order to inform future reviews by NSIRA.
(TS) The Office of the Communications Security Establishment Commissioner (OCSEC) previously studied the sharing of, and access to, cyber threat information between CSE’s SIGINT and IT Security Branches. OCSEC’s review found that CSE’s cyber threat information sharing and accessing activities between CSE’s SIGINT and IT Security were consistent with National Defence Act and Privacy Act authorities, and that information shared between the branches posed a minimal risk to the privacy of Canadians.
(U) With the coming into force of the CSE Act, on August 1, 2019, CSE’s legal authorities for conducting its activities have changed since OCSEC’s review. In light of this change of legal authority for CSE, NSIRA decided to re-assess and evaluate whether CSE’s internal information sharing activities between the FI and cybersecurity aspects are consistent with the CSE Act and the Privacy Act.
(U) NSIRA expects that CSE’s internal sharing of IRTC complies with the CSE Act and the Privacy Act. As such, the focus of this review was to examine the legal authority that allows for CSE to share IRTC between the FI and cybersecurity aspects.
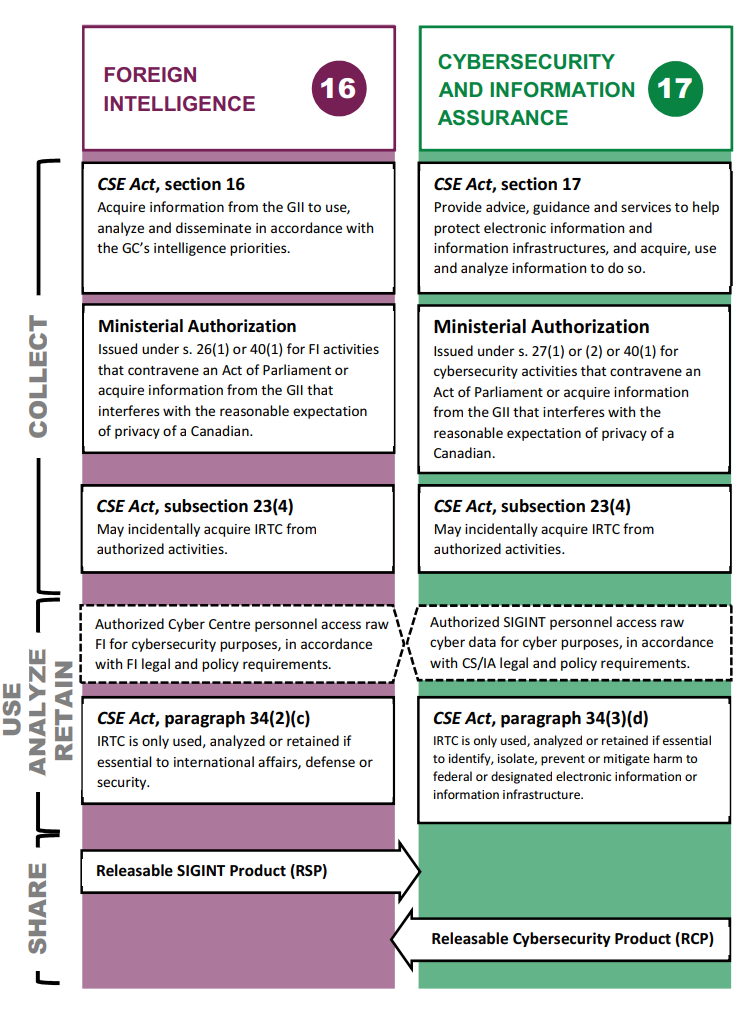
(U) The Communications Security Establishment Act (CSE Act), creates five distinct aspects to CSE’s mandate. The CSE Act distinguishes between each aspect and its associated activities, as listed below: Foreign intelligence (FI) (section 16): to acquire information from the global information infrastructure (GII), and to use, analyse and disseminate the information for the purpose of providing foreign intelligence;
- Foreign intelligence (FI) (section 16): to acquire information from the global information infrastructure (GII), and to use, analyse and disseminate the information for the purpose of providing foreign intelligence;
- Cybersecurity and information assurance (cybersecurity) (section 17): to provide advice, guidance and services to help protect electronic information and information infrastructures of federal institutions or those designated under subsection 21(1) of the CSE Act, and to acquire, use and analyse information to do so;
- Defensive cyber operations (section 18): to carry out activities on the GII to help protect electronic information and information infrastructures of federal institutions or those designated under subsection 21(1) of the CSE Act;
- Active cyber operations (section 19): to carry out activities on the GII to degrade, disrupt, influence, respond to or interfere with the capabilities, intentions or activities of foreign entities; and
- Technical and operational assistance (section 20): to provide technical and operational assistance to federal law enforcement, security agencies, the Canadian Armed Forces and the Department of National Defence.
(U) The CSE Act also distinguishes between the aspects by requiring different Ministerial Authorizations (MAs) for CSE’s activities, except for assistance activities (s. 20). Under the CSE Act, and with the exception of assistance activities, CSE’s activities must not be directed at a Canadian or any person in Canada, and must not infringe the Canadian Charter of Rights and Freedoms. Under the FI and cybersecurity aspects, CSE’s activities must not contravene any other Act of Parliament or involve the acquisition of information on or through the GII that interferes with the reasonable expectation of privacy of a Canadian or a person in Canada, unless carried out under a MA.
(U) The Minister of National Defence may issue a MA that permits CSE to conduct activities or classes of activities that may contravene any other Acts of Parliament, and, in the case of FI and cybersecurity, would involve the acquisition of information that would interfere with the reasonable expectation of privacy of a Canadian or a person in Canada. FI and cybersecurity MAs must be approved by the Intelligence Commissioner (IC), who must review whether the conclusions made by the Minister in issuing the authorization are reasonable.
(U) Thus, CSE is permitted to incidentally acquire information relating to a Canadian or a person in Canada in the course of carrying out activities that are authorized by an FI (s. 26(1)), cybersecurity (s. 27(1) or 27(2)), or emergency (s. 40) MA. CSE refers to this information as information relating to a Canadian or a person in Canada (IRTC). In order to issue an authorization, the Minister must be satisfied that CSE will only use, analyse or retain IRTC when it meets the “essentiality” conditions in section 34 of the CSE Act, which are different for the FI and cybersecurity aspects. For FI, “essentiality” means an assessment of whether the information is essential to international affairs, defence or security. For cybersecurity, “essentiality” means an assessment of whether the information is essential to identify, isolate, prevent or mitigate harm to (i) federal institutions’ electronic information or information infrastructures, or (ii) electronic information or information infrastructures designated under subsection 21(1) of the CSE Act.
(U) As the CSE Act distinguishes between the aspects and the corresponding MAs, NSIRA examined CSE’s legal authority for sharing IRTC between the FI and cybersecurity aspects.
(U) Due to operational and access-related challenges, including due to the COVID-19 pandemic, this review was not able to independently assess and verify CSE’s compliance with the law or compliance with the restrictions and authorities in place when internally sharing and using information between aspects. Additionally, NSIRA was not able to independently observe, investigate or validate the systems used when sharing data between aspects (consult Annex F for a description of processes and methods used by CSE to share information between the two aspects). These data sharing systems may be examined in future NSIRA reviews.
(U) NSIRA also intended to review the internal sharing of information with the active (ACO) and defensive (DCO) cyber operations aspects of CSE’s mandate, including compliance with the requirements in subsection 34(4) of the CSE Act on acquiring information while conducting ACO and DCO cyber operations. Among other things, this subsection stipulates that no information may be acquired pursuant to ACO and DCO authorizations unless done in accordance with an FI (CSE Act, s. 26(1)), cybersecurity (CSE Act, ss. 27(1) & 27(2)), or emergency (CSE Act, s. 40(1)) authorization. This facet of the review was instead covered in NSIRA’s review of CSE’s Active Cyber Operations and Defensive Cyber Operations – Governance, and will be further examined in NSIRA’s second review of ACO and DCO activities later in 2021.
(U) Importantly, this review did not examine the disclosure of Canadian identifying information (CII) outside of CSE.
Background
What is IRTC?
(U) While the CSE Act mentions IRTC several times, it is not clearly defined. In practice, IRTC is the information about Canadians or persons in Canada that may be incidentally collected by CSE while conducting FI or cybersecurity activities under the authority of an MA. According to CSE policy, IRTC is any information recognized as having reference to a Canadian or person in Canada, regardless of whether that information could be used to identify that Canadian or person in Canada.
(U) There is a distinction to be made between IRTC and Canadian identifying information (CII). For example, the CSE Act uses both IRTC and CII throughout the Act to describe types of information. Where IRTC is any information recognized as having reference to a Canadian or a person in Canada, CII is information that could be used to identify a Canadian or a person in Canada and that has been used, analyzed or retained under a FI or emergency authorization. CSE describes CII as a subset of IRTC. CII may be disclosed by CSE to designated persons under section 43 of the CSE Act.
Internal Sharing of IRTC at CSE
(TS) In some circumstances, CSE policy allows for IRTC collected under the authority of one aspect to be shared for use under another aspect (see Annex D for a description of the other types of information that is shared between the FI and cybersecurity aspects). CSE policy permits FI to be used internally to fulfill cybersecurity requirements. Information retained under the cybersecurity aspect may be used by CSE personnel operating under the FI aspect, unless the information is subject to any conditions imposed on it by external clients or disclosing entities. According to CSE, sharing information across aspects of the mandate enables CSE to carry out its activities in support of Government of Canada priorities.
(TS) In the cybersecurity context, CSE explained that any IRTC shared internally in support of the FI aspect [redacted description of CSE operations]
(TS//SI) An example that CSE provided [redacted example of CSE operations]. Sharing this information across the aspects of the mandate enabled CSE to help protect GC information and information infrastructures as well as those of Systems of Importance (SOI), by identifying, isolating and mitigating the threat, and provided GC decision- makers with a comprehensive view of the foreign threats targeting Canada.
(TS) After reviewing a random selection of reports, in addition to receiving information by CSE and interviewing analysts familiar with working on both FI and cybersecurity, NSIRA learned that the IRTC shared between the FI and cybersecurity aspects generally included: [redacted list of operational utilized in the system]. CSE policy permits [redacted].
(U) CSE asserts that although IRTC is shared across the aspects, activities will not be directed at Canadians or persons in Canada. As previously mentioned, CSE must not direct its activities at a Canadian or any person in Canada.
Findings and recommendations
Compliance with the CSE Act and the Privacy Act
What Acts Apply to the Internal Sharing of Information?
(S) The relevant statutes that apply to CSE’s internal information sharing are CSE’s enabling statute, the CSE Act, and the Privacy Act. The CSE Act does not provide a clear authority to share IRTC between the aspects. Likewise, the CSE Act disclosure provisions for CII in sections 43–45 do not prima facie contemplate internal sharing of IRTC, as to disclose information under these provisions, the Minister would need to authorize CSE to collect and disclose CII to itself. Additionally, CSE is not a designated entity under section 45 of the CSE Act for the purposes of receiving disclosed information under sections 43 and 44.
(U) IRTC could constitute personal information as defined in section 3 of the Privacy Act, which is information about an identifiable individual that is recorded in any form. For example, Canadian IP addresses, may constitute both IRTC for the purposes of the CSE Act and personal information under the Privacy Act. Pursuant to section 4 of the Privacy Act, the collection of personal information must relate directly to an operating program or activity of the institution, which includes CSE’s mandated activities in the CSE Act.
(U) The Privacy Act also requires that personal information be used and disclosed in manner consistent with sections 7 and 8 of the Privacy Act. For reference, Section 7 of the Privacy Act states:
Personal information under the control of a government institution shall not, without the consent of the individual to whom it relates, be used by the institution except
- For the purpose for which the information was obtained or compiled by the institution or for a use consistent with that purpose; or
- For a purpose for which the information may be disclosed to the institution under subsection 8(2).
(U) NSIRA examined whether CSE’s internal sharing of IRTC is consistent with the Privacy Act, which limits how collected personal information can be used by a federal institution. NSIRA concluded that in some circumstances, as described later in the report, internal sharing of IRTC that constitutes personal information between the FI and cybersecurity aspects might satisfy Privacy Act requirements. This compliance assessment requires a case-by-case analysis.
CSE Directorate of Legal Services’ (DLS) Legal Analysis
(Protected B//Solicitor-Client Privilege) NSIRA examined CSE DLS’s legal analysis, provided by Department of Justice (DOJ) lawyers, [redacted legal opinion or advice].
(Protected B//Solicitor-Client Privilege) In DOJ’s opinion, [redacted legal opinion or advice].
(Protected B//Solicitor-Client Privilege) According to DOJ, [redacted legal opinion or advice].
Compliance with the Privacy Act
(U) NSIRA observes that, in assessing compliance with section 7 of the Privacy Act, CSE emphasizes compliance with paragraphs 34(2)(c) and 34(3)(d) of the CSE Act to support the internal sharing of personal information across the various aspects of the mandate.
(U) As noted, section 7 of the Privacy Act requires that personal information under the control of a government institution shall not be used without the consent of an individual, except for two purposes: (1) the purpose for which it was obtained, or for a use consistent with that purpose; or (2) for a purpose for which the information may be disclosed to the institution under subsection 8(2) of the Act. Importantly, a use of information need not be identical to the purpose for which information was obtained; it must only be consistent with that purpose.
(U) CSE’s reliance on section 34 of the CSE Act poses a challenge for compliance with the Privacy Act because section 34 does not identify the actual purpose of the incidental collection of the IRTC, or provide an authority for internal sharing. Rather, section 34 conditions the Minister’s authority to issue an MA on prerequisites. Paragraphs 34(2)(c) and 34(3)(d) of the CSE Act specify that the Minister must be satisfied that the privacy protection measures in section 24 of the Act will ensure that IRTC will be used, analysed, and retained only if it complies with the respective essentiality requirements for FI and cybersecurity, as the case may be. These conditions establish a required threshold for the use, analysis and retention of IRTC collected under a MA, and not an authority for internal sharing of IRTC.
(U) Depending on the factual circumstances in which the IRTC is shared, CSE’s sharing of IRTC that constitutes personal information between the FI and cybersecurity aspects could be supported by the CSE Act and the Privacy Act when the information is shared for the purpose for which it was obtained, or for a use consistent with that purpose. This would require a case-by- case assessment to ensure that the purpose for which the IRTC is shared internally is for the same purpose for which it was collected, a purpose consistent with that original purpose for collection, or as permitted by section 7(b), that the sharing is permitted for one of the reasons identified by Parliament in subsection 8(2) of the Privacy Act. As mentioned, CSE does not consider internal sharing a disclosure of information. NSIRA notes that the issue of whether internal sharing in this way constitutes a “use” or a “disclosure”, under the Privacy Act is unclear. Regardless, NSIRA observes that in relying solely on the “essentiality” criteria in section 34, CSE is not assuring itself that it has lawful authority for internal sharing.
(U) A justification under section 7(a) or paragraph 8(2)(a) of the Privacy Act requires CSE to identify the purpose of the incidental collection and internal sharing, which is found in the corresponding aspect of CSE’s mandate. CSE’s purpose for collecting, and authority to collect, personal information comes from the CSE Act. Sections 16 and 17 of the Act identify FI and cybersecurity as operating programs and activities of the institution, and provide the authority to collect information for those purposes. As noted, MAs must authorize collection when activities might contravene any other Act of Parliament, or involve the acquisition of information from or through the GII that interferes with a reasonable expectation of privacy of a Canadian or a person in Canada. From the descriptions of the aspects in sections 16 and 17 of the CSE Act, there may be instances where information acquired under one aspect can be used for the same, or a consistent purpose, as exists for another, thus satisfying Privacy Act requirements for sharing information internally. However, this cannot simply be assumed as the purposes of the aspects are described differently within the Act.
(U) Section 16 of the CSE Act authorizes CSE to acquire information from or through the GII, and to use, analyse and disseminate the information for the purpose of providing foreign intelligence in accordance with Government of Canada (GC) priorities. Section 17 of the CSE Act, in turn, authorizes CSE to provide advice, guidance and services to help protect the electronic information or information infrastructures of federal institutions and designated systems of importance, and to acquire, use and analyse information, from the GII or from other sources, in order to provide such advice, guidance and services.
(TS//SI) When sharing FI-acquired IRTC to support CSE’s cybersecurity aspect, there is arguably no shift in purpose if cybersecurity is among the purposes for which the FI is obtained, used, analysed and disseminated. For the period of this review, [redacted related to GC priorities]. Sharing FI information to fulfill CSE’s section 17 cybersecurity objectives of providing advice, guidance and services to help protect federal and designated electronic information and infrastructures could be considered as the same purpose, or consistent with the purpose, for which the IRTC was originally obtained. Where the FI is used in the section 17 aspect to protect federal and designated electronic information and infrastructures, the purpose of collection and the subsequent use of that information could remain the same.
(U) For cybersecurity-acquired IRTC, sharing information to the FI aspect could be permissible if the FI purpose is the same as, or consistent with, the purpose for which the information was initially acquired, i.e., for the purpose of providing advice, guidance and services to help protect federal and designated information infrastructures or electronic information. Thus, sharing cybersecurity IRTC to the FI aspect would be permissible under the Privacy Act if the internal sharing ultimately serves the purpose of helping to protect federal and designated information infrastructures or electronic information.
(U) In sum, if the purpose of CSE’s acquisition of personal information is for the purpose of, or consistent with, delivering on the foreign intelligence and/or cybersecurity aspects, CSE’s internal sharing of IRTC can be consistent with section 7(a) or paragraph 8(2)(a) of the Privacy Act, provided that purpose of the information collection and sharing is identified and justified. CSE must also always satisfy any conditions from the CSE Act and relevant MAs on the collection and use of IRTC. To support internal sharing of personal information between the aspects, further analysis is required based on the factual circumstances of each case.
Finding no. 1: CSE’s internal sharing of information between the FI and cybersecurity aspects of the mandate has not been sufficiently examined for compliance with the Privacy Act.
Recommendation no. 1: CSE should obtain additional legal advice on its internal sharing of information between the foreign intelligence and cybersecurity aspects of the mandate, explicitly in relation to compliance with the Privacy Act, which thoroughly addresses the following two issues:
- Whether the internal sharing of information between the foreign intelligence and cybersecurity aspects of the mandate is a use or a disclosure of information for the purposes of the Privacy Act; and
- Whether uses and disclosures are done in accordance with sections 7 and 8 of the Privacy Act.
The Ministerial Authorizations
(U) The CSE Act does not allow the Minister to authorize internal sharing of IRTC, as MAs may only authorize, in the case of FI, the activities or classes of activities listed in subsection 26(2), or for cybersecurity, access and acquisition of the information referred to in subsections 27(1) and 27(2). Any internal sharing of IRTC that constitutes personal information must be done in accordance with the Privacy Act.
(U) As mentioned, section 24 of the CSE Act requires CSE to have measures in place to protect the privacy of Canadians and of persons in Canada in the use, analysis, retention and disclosure of IRTC. When issuing a MA, the Minister must conclude that these measures will ensure that any acquired IRTC will only be used, analysed or retained if it meets the essentiality thresholds in paragraphs 34(2)(c) or 34(3)(d). The Minister may issue these authorizations if they are of the view that such activities would be “reasonable and proportionate, having regard to the nature of the objective to be achieved and the nature of the activities.” As the Minister considers the reasonableness of the activities proposed against either an FI or cybersecurity purpose, it is conceivable that some activities might be reasonable and proportionate in one context, but not in the other. As activities authorized under subsection 26(2) might acquire a broader range of information than what is contemplated in subsections 27(1) and 27(2), the sharing of FI to cybersecurity might allow for CSE to use more information for a cybersecurity purpose than what is permitted under cybersecurity authorizations alone, and may require different privacy protection measures when using such information.
(U) To issue an MA, the Chief of CSE must set out the facts in an application that would allow the Minister to conclude that there are reasonable grounds to believe that the authorization is necessary, and that the conditions for issuing it are met. NSIRA considers it necessary for the Chief’s application to fully inform the Minister of how IRTC might be used and analysed by CSE, including the sharing of IRTC to another aspect, and for what purpose. This information would also allow for the Minister to make a determination under section 35 whether any other terms, conditions, or restrictions are advisable to protect the privacy of Canadians when issuing a FI or cybersecurity authorization.
(TS//SI) For the authorizations issued during 2020, most of the Chief of CSE’s applications indicated that collected and retained information might be used under a different aspect, while the text of most of the corresponding MAs did not mention use under a different aspect. This situation was reversed in one instance: [redacted example of CSE operations].
(TS//SI) Moreover, the 2020 FI applications and authorizations indicate that in order to meet the essentiality condition for retention of IRTC under subsection 34(2)(c) of the CSE Act, IRTC will be retained if it is assessed as essential to cybersecurity. In these instances, cybersecurity is included under the concept of “essential to security”, thus providing the Minister with additional context as to how the essentiality conditions are assessed and met by CSE. NSIRA considers this information necessary for the Minister to assess whether the conditions listed in section 34 of the CSE Act for issuing the authorization are met.
Finding no. 2: With one exception, the Chief of CSE’s applications for Ministerial Authorizations issued in 2020 informed the Minister of National Defence that retained information might be used to support a different aspect.
Finding no. 3: The applications for foreign intelligence authorizations by the Chief of CSE for the period of review appropriately informed the Minister of National Defence how the essentiality condition in paragraph 34(2)(c) is met for IRTC collected under the FI aspect.
Recommendation no. 2: All foreign intelligence and cybersecurity applications from the Chief of CSE should appropriately inform the Minister of National Defence that retained information might be used to support a different aspect.
Assessment of Essentiality, Necessity, and Relevancy
(U) Under CSE policy, an assessment of IRTC’s relevance, essentiality, or necessity to each aspect is required for sharing information across the aspects (see Annex G for CSE’s policy thresholds and definitions used to assess IRTC when shared between the aspects). These terms come from the CSE Act, but are not defined in the Act. CSE policy offers definitions and criteria for assessing and applying these thresholds to the information. NSIRA did not assess these policy thresholds or definitions for lawfulness, or how these requirements are satisfied by CSE when internally sharing IRTC. This may be examined in future reviews.
(TS) CSE policy also sets forth the criteria by which to authorize the sharing of IRTC across aspects (see Annex E for the approval processes at CSE for sharing information). Before any IRTC may be shared across aspects of the mandate, the information must be assessed for essentiality to the aspect for which it was acquired. If it does not pass this initial essentiality threshold, the information must be deleted.
(Protected B//Solicitor-Client Privilege) According to CSE, [redacted legal opinion or advice]
(U) NSIRA agrees that the CSE Act does not require that internally shared IRTC between the FI and cybersecurity aspects meet both of the essentiality conditions of paragraphs 34(2)(c) and 34(3)(d) of the CSE Act. Subsections 22(3) and 22(4) of the CSE Act require an FI or cybersecurity MA when the activities carried out in furtherance of either aspect involve acquiring information from the GII that may interfere with a reasonable expectation of privacy, or for activities that might contravene an Act of Parliament. MAs may only authorize the activities or classes of activities listed in subsection 26(2) for FI, or to access information infrastructures and acquire the information referred to in subsections 27(1) and 27(2). As mentioned, the “essentiality” thresholds in section 34 condition the Minister’s authority to issue an MA on the prerequisite of the privacy protection measures in section 24. Such a requirement can be understood as applying to use, analysis and retention of IRTC collected by CSE under the authority of a MA and within the confines of a single aspect. Therefore, there is no legal requirement within the CSE Act that CSE observe the essentiality threshold of the aspect of which the IRTC is internally shared. IRTC must only meet the original essentiality condition of either paragraph 34(2)(c) or 34(3)(d) when IRTC is acquired, as required by the MA authorizing its actual incidental collection.
Finding no. 4: CSE’s position that they do not need to assess “essentiality” twice when sharing information between the foreign intelligence and cybersecurity aspects of the mandate is compliant with paragraphs 34(2)(c) and 34(3)(d) of the CSE Act.
Conclusion
(U) As the CSE Act distinguishes between the aspects and the corresponding MAs, NSIRA examined CSE’s legal authority for sharing IRTC between the FI and cybersecurity aspects of its mandate. NSIRA concludes that internal sharing may be consistent with the Privacy Act in some circumstances. However, CSE must give further consideration to the purpose of the collection of the IRTC to justify any internal sharing of IRTC.
(U) This review also established a foundational understanding of some of the processes, systems, and compliance measures applied by CSE when sharing IRTC across aspects. Although NSIRA was not able to independently verify this information, NSIRA intends to build upon this information in future reviews.
Annexes
ANNEX A: Objectives, Scope, and Methodology
(U) Initially, NSIRA intended to examine the internal sharing of IRTC between aspects of CSE’s mandate in a thematic manner that covered several operational areas and several aspects. The review intended to examine the sharing of information between aspects of CSE’s mandate for the period of August 1, 2019 to August 1, 2020, with the objective to independently assess and evaluate:
- Compliance with legal, ministerial, and policy requirements, including adequate management of compliance risks when conducting information sharing activities between aspects of CSE’s mandate; and,
- CSE’s policies, procedures and practices on the internal sharing of information between aspects of the mandate.
(U) Due to operational realities, including COVID-19 related disruptions and access challenges, the objectives, scope, and methodology of this review were significantly reduced from the original Terms of Reference (sent to CSE on August 28, 2020), to focus mainly on the legal authority for sharing of information between the FI and cybersecurity aspects.
(U) For this review, NSIRA examined documents and records relevant to the sharing of information between aspects of CSE’s mandate, from the coming into force of the CSE Act on August 1, 2019, until August 1, 2020.
(U) Two interviews were conducted with CSE employees involved with information sharing across CSE’s aspects, and an interview was conducted with a Department of Justice lawyer in CSE’s Directorate of Legal Services familiar with the legal framework of such activities.
(U) NSIRA also completed a foundational description of some of the processes, systems, and compliance measures in place when sharing such information, in order to establish a baseline of knowledge to inform future reviews.
ANNEX B: Meetings and Briefings
Briefing. “Information Sharing: Sharing information for use across aspects of the CSE Mandate”, NSIRA Briefing, February 7, 2020.
NSIRA meeting with counsel from the Department of Justice at CSE DLS, October 13, 2020.
NSIRA meeting with CSE analysts, October 20, 2020.
ANNEX C: Findings and Recommendations
Finding no. 1: CSE’s internal sharing of information between the FI and cybersecurity aspects of the mandate has not been sufficiently examined for compliance with the Privacy Act.
Recommendation no. 1: CSE should obtain additional legal advice on its internal sharing of information between the foreign intelligence and cybersecurity aspects of the mandate, explicitly in relation to compliance with the Privacy Act, which thoroughly addresses the following two issues:
- Whether the internal sharing of information between the foreign intelligence and cybersecurity aspects of the mandate is a use or a disclosure of information for the purposes of the Privacy Act; and
- Whether uses and disclosures are done in accordance with sections 7 and 8 of the Privacy Act.
Finding no. 2: With one exception, the Chief of CSE’s applications for Ministerial Authorizations issued in 2020 appropriately informed the Minister of National Defence that retained information might be used to support a different aspect.
Finding no. 3: The applications for foreign intelligence authorizations by the Chief of CSE for the period of review appropriately informed the Minister of National Defence how the essentiality condition in paragraph 34(2)(c) is met for IRTC collected under the FI aspect.
Recommendation no. 2: All foreign intelligence and cybersecurity applications from the Chief of CSE should appropriately inform the Minister of National Defence that retained information might be used to support a different aspect.
Finding no. 4: CSE’s position that they do not need to assess “essentiality” twice when sharing information between the foreign intelligence and cybersecurity aspects of the mandate is compliant with paragraphs 34(2)(c) and 34(3)(d) of the CSE Act.
ANNEX D: Partner and client information and publicly available information shared between the fi and cybersecurity aspects
(Protected B) Under the cybersecurity aspect, federal and non-federal clients may disclose cyber threat information to CSE as Canada’s lead agency for cybersecurity, or when seeking CSE services to analyse and mitigate known or suspected cyber incidents. Disclosed information may be used for FI purposes provided that it is done so for the purposes of identifying, isolating, preventing or mitigating harm to federal systems or systems of importance to the GC.
(Protected B) The documentation that governs CSE’s arrangements with GC and non- federal clients specifies that information obtained by CSE from a given client’s network or system that is relevant to the cybersecurity aspect may be shared with partners [redacted CSE operational information] or internal partners for GC clients) involved in cybersecurity for the purposes of identifying, isolating, preventing or mitigating harm to federal systems or systems of importance to the GC. However, this type of documentation does not explicitly mention that clients’ information might be used for FI purposes. For the purposes of obtaining the informed consent of disclosing entities, NSIRA considers it appropriate for CSE to be fully transparent with how clients’ information might be used by CSE.
(Protected B) When client information is shared with [redacted CSE operational information] partners, the information is anonymized and identifiable information is omitted. Any releasable cybersecurity products created from client information must only contain information necessary to mitigate a cyber compromise. Additionally, disclosing entities may also impose specific restrictions on the use and sharing of their data at the time of disclosure.
(TS) As per subsection 21(1) of the CSE Act, CSE is permitted to acquire and use publicly available information without seeking a MA. Currently, [redacted related to legal opinion or advice].
ANNEX E: Approval Process and Sharing Release Approvals
Approval Processes for Sharing IRTC
(TS//SI) The appropriate approval authority for sharing information is outlined in CSE internal policy, where the nature of the information dictates the release authority. CSE policy requires management approval (known as the release authorities) before sharing unsuppressed IRTC between aspects. However, policy does not stipulate the actual process for approval; this is determined by the relevant operational areas in accordance with their business practices. The Mission Policy Suite (MPS) requires all management decisions to be documented and retained in a central repository for transparency and accountability purposes. Those records must be accessible for review purposes. However, for this review, NSIRA was unable to independently verify and assess the approval process for internally shared IRTC.
(TS) Generally, CSE requires management approval for sharing information contained within a report for use across aspects of the mandate, and will elevate the appropriate release authority when the information contains IRTC. The appropriate release authority and conditions for release are outlined in policy (discussed below). The release authority is responsible for the information exchange, and must be informed if any changes are made to the data that result in a change in the type of privacy-related information to be shared.
(TS) Automated sharing techniques [redacted related to GC priorities].
Cybersecurity IRTC to Foreign Intelligence
(U) Retained IRTC under the cybersecurity aspect can be shared to FI as a Releasable Cybersecurity Product (RCP), which must meet the requirements listed below. The release authority is determined by the privacy impact that the release of information may have on an individual or entity, which is in turn determined by the level of sensitivity and privacy impact of the IRTC. Depending on the level of sensitivity of the IRTC, operational managers or supervisors from the Canadian Centre for Cyber Security (CCCS, or Cyber Centre) must approve RCPs containing IRTC.
(U) The requirements for a RCP as per CSE policy include the following:
| Requirement | When and How the Requirement is Applied |
|---|---|
| Purpose is to provide advice, guidance, and services | At the time of sharing – why am I sharing this information? |
| Product only contains retained information | The decision to use and retain information is made at the time the raw data is assessed for relevance and necessity (and in the case of IRTC, essentiality) to the cybersecurity aspect of the mandate. |
| Privacy Protection | At the time of sharing, as appropriate (e.g., being shared back with the system owner/administrator who already has access to the information on their own systems; or to a broader audience with strict limits on the use of the information). No suppression is required if the IRTC is shared for use under the FI aspect of the mandate when the sharing is for the purposes of supporting activities to help protect the electronic information and information infrastructures of the GC or SOI to the GC |
| Classification and limitations on use and handling | Either at the time of sharing, or applied at a later stage to the onward use and dissemination of the information by FI. Can include pre-approved uses and conditions, as well as limitations placed by the data/system owner if applicable. Can be applied by report-authoring platforms to End Product Reports (EPRs), restrict the use and dissemination of CSE information. |
| Auditable | At the time of acquisition, applied automatically by CSE systems. All data entering CSE is automatically tagged with a unique identifier, as well as information regarding origin (e.g., MA vs non-MA, disclosing client if applicable etc.), access restrictions if applicable, aspect of the mandate under which the data was acquired, date and time of acquisition, use and handling requirements. |
| Approved for release | At the time of sharing. The approval authority depends on the nature of the information. See table in s. 25.2 in the MPS cybersecurity chapter. |
Foreign Intelligence IRTC to Cybersecurity
(TS) IRTC under the FI aspect can be released to CCCS as a Releasable SIGINT Product (RSP). RSPs that contain information with a recognized Canadian privacy interest, or based on material with a Canadian privacy interest, require DC SIGINT approval for release, which can be delegated.
(TS) In order to create a RSP to share information for use under the cybersecurity aspect, the following table summarizes how the criteria required in policy must be met:
| Requirement | When and How the Requirement is Applied |
|---|---|
| Information is relevant to FI | At the time of assessment. Must be met prior to use. |
| Privacy protection e.g., suppression of IRTC | At the time of sharing, if necessary. Suppression is mandatory for IRTC included in an EPR shared outside CSE. CCCS clients that receive these EPRs may request this CII through the regular Action-On process. Otherwise, no suppression required if IRTC is necessary for cybersecurity purposes, but other measures to protect privacy are used, for example, restricting the audience for the information. |
| Sanitization | Either at the time of sharing, or to be applied if/when cybersecurity use requires the information be sanitized to protect CSE equities. |
| Serialization | At the time of acquisition, applied automatically by CSE systems. All data entering CSE is automatically tagged with a unique identifier, as well as information regarding origin [redacted example of CSE operations] access restrictions if applicable, aspect of the mandate under which the data was acquired, date and time of acquisition, use and handling requirements. |
| Caveats | Either at the time of sharing, or applied at a later stage to the onward use and dissemination of the information by cybersecurity. Can include pre- approved actions-on. Automatically applied by report-authoring platforms to EPRs, limit the use and dissemination of CSE information. |
| Approved for release | At the time of sharing. The approval authority depends on the nature of the information. See table in s. 27.8 of MPS FI chapter. |
Internal Reviews of Information Sharing
(TS) Internal sharing of information between the aspects is subject to CSE internal review, for both automated sharing and data-based queries. SIGINT Compliance, the group responsible for internal compliance activities under the FI aspect, reviewed CSE-originated queries for 2019 and 2020, and found that query activity was complaint. The CCCS’ Internal Program for Operational Compliance (IPOC) did not prioritize compliance monitoring reviews for the past two fiscal years in order to monitor other activities that posed a higher-risk to compliance.
(TS) Automated sharing techniques are also subject to review. SIGINT Compliance is required to revalidate all instances of automated sharing between the FI and cybersecurity aspects every 12 months. The most recent review for the period of July 2019 to September 2020 found that the [redacted number] of automated sharing were compliant with policy requirements, except for [redacted number] that CSE was unable to assess.
ANNEX F: Methods and processes of sharing
(TS) This section describes the methods and processes used by CSE to share information between the FI and cybersecurity aspects. There is a multitude of systems, methods, and processes that enable information sharing between these aspects, both suppressed and unsuppressed. Note that the processes described below are not static, and that CSE’s systems, methods, and processes can change anytime.
(TS) Generally, access to information for each aspect is restricted by [redacted related to legal opinion or advice]
(TS//SI) For examples, [redacted description of CSE operations].
(U) As required by section 24 of the CSE Act, CSE must have measures in place to protect the privacy of Canadians and persons in Canada in the use of information related to them acquired in furtherance of the FI or cybersecurity aspects.
(TS) Suppression and minimization of IRTC is not required by CSE policy when sharing information internally; it is a default practice to share IRTC unsuppressed across the FI and cybersecurity aspects. According to CSE, although not mandated by policy, analysts are encouraged to anonymize or remove privacy-related information where it is not essential for the person using the information to understand the context and value. CSE recognizes that suppression and minimization are a best effort practice, and is of the opinion that CSE is not in contravention of the law should suppression, minimization, anonymization not occur when sharing information between the aspects.
Cross-Aspect Access to both SIGINT and Cyber Centre Raw Data
(TS) When accessing data from another aspect that is not within a reporting product (i.e., RSPs or RCPs), analysts are subject to the policy requirements of the data they are accessing.
(TS//SI) Under the FI aspect, [redacted description of CSE operations].
(TS//SI) For examples, [redacted description of CSE].
(TS//SI) While analysing raw FI data, Cyber Centre personnel must follow all applicable foreign intelligence authorities and policy requirements. The use, handling, and retention of this information is further subject to any restrictions applied to the foreign intelligence data.
(TS//SI) SIGINT personnel may access and use Cyber Centre systems if they meet the requirements in section 26.1 of the MPS Cybersecurity. Access to Cyber Centre systems and raw cybersecurity data is similarly restricted [redacted] to individuals with an operational need-to-know and mandatory annual policy and compliance training and knowledge testing. [description of CSE operations].
Reporting – RCPs and RSPs
(U) Retained information is internally shared through formal reporting processes in the form of either RSPs, which includes EPRs, or RCPs.
(TS//SI) Cyber Centre personnel operating under cybersecurity requirements may also be internal clients without access to raw FI data. Foreign intelligence information is shared to some cybersecurity personnel as an RSP, meaning that the information has met the requirements for release in CSE policy, including suppression and approval, and is subject to any restrictions on the intelligence data. For the period of review, there [redacted number] RSPs approved for release from the FI aspect that were made available to personnel operating under the cybersecurity aspect.
(TS//SI) Cybersecurity information can be reported and released to SIGINT personnel for subsequent use under the FI aspect via RCPs. Information released through RCPs must meet the requirements for release within CSE policy, and the use must be consistent with the cybersecurity aspect of CSE’s mandate and used for a subsequent use related to relevant GC priorities. For the period of review, [redacted number] RCPs were disseminated to authorized recipients in SIGINT.
Receiving Suppressed Identifiers from Reporting
(TS) Suppressed IRTC in EPRs disseminated through SLINGSHOT can be requested by internal CSE clients through the existing CII external disclosures process. This is the only mechanism by which suppressed identities can be accessed and released. Supressed IRTC can be requested by submitting a request to the Action-On team (D2A). The requestor must provide the legal authority and operational justification to receive the unsuppressed information. Between August 1, 2019 and August 1, 2020, [redacted description of CSE operations].
(TS) Although the mechanism for releasing this information is the same as the external disclosures process, it is not considered a “disclosure” of information but an internal “use” of information. As such, the disclosure regime requirements of sections 43 to 46 of the CSE Act do not need to be met in order for supressed information to be released to internal CSE clients.
Joint-Reporting
(TS//SI) Information may also be shared between the foreign intelligence and cybersecurity aspects for the purposes of disseminating foreign intelligence under cybersecurity authorities. This foreign intelligence information must first be used for foreign intelligence purposes, and then may be shared to CCCS personnel use under the cybersecurity aspect and only then released under their authorities.
(TS//SI) Approval for sharing of foreign intelligence information under the cybersecurity aspect of the mandate must abide by the appropriate release approval authorities for both aspects. [redacted description of CSE operations]
Automated Sharing (forms of RSP or RCP)
(TS) Automated sharing is defined in CSE policy as “the use of automated techniques or processes to expedite the dissemination of [redacted releasable reporting products]”.
(TS//SI) There are various automated feeds used at CSE to exchange information between the aspects. [redacted description of CSE operations].
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted]
(TS//SI) [redacted description of CSE operations and systems]
(TS//SI) [redacted description of CSE operations and systems]
Other Methods of Sharing
(TS) More informal methods of information exchange may occur between the two aspects. As CSE teams work closely together, analysts might gain knowledge of information that can be useful for either aspect of the mandate. Analysts may exchange general knowledge without any formal reporting. CSE policy provides for analytic exchanges whereby analysts may engage with partners working under a different aspect to work on common objectives by exchanging information. However, any data exchange must meet the requirements of issuing a RCP or RSP, although the data need not be released through the formal product dissemination systems.
ANNEX G: Policy Thresholds for Internal Sharing
(U) Generally, CSE policy provides that IRTC may be shared internally according to the thresholds outlined below. As mentioned, NSIRA did not assess these thresholds or definitions for lawfulness, but may do so in future reviews. Additionally, NSIRA did not assess how these policy requirements are satisfied in practice.
Foreign Intelligence Aspect to Cybersecurity Aspect
(TS) Under the FI aspect, IRTC must be essential and relevant to the FI aspect prior to sharing, as per the essentiality condition in 34(2)(c) of the CSE Act. According to CSE policy, the information must be considered essential to international affairs, defence or security, including cybersecurity. Essential is not defined in CSE policy, though policy provides criteria by which to assess the IRTC as it relates to protecting the lives or safety of individuals, or to serious criminal activity relating to the security of Canada.
(TS) To share FI IRTC information for use under the cybersecurity aspect of the mandate, the IRTC information must be relevant to the cybersecurity aspect. IRTC must further be assessed for necessity to the cybersecurity aspect, meaning whether the information is necessary to help protect GC systems and designated systems of importance. It is a policy decision to apply the threshold of necessity from subsection 44(1) of the CSE Act.
(TS) CSE policy requires the standard of necessity, [redacted description of CSE operations]. This information is necessary to fulfill the cybersecurity mandate as it enables activities that protect GC systems and designated SOIs (such as by blocking traffic). However, the identifiable individual or entity is not the focus of the activity.104 Therefore, CSE is of the opinion that since there is a lower risk to the reasonable expectation of privacy of the individual in the cybersecurity context, the threshold of necessity is sufficient for sharing FI-acquired IRTC to the cybersecurity aspect.
Cybersecurity Aspect to Foreign Intelligence aspect
(TS//SI) Under the cybersecurity aspect, IRTC acquired under a MA must be both relevant and essential prior to sharing, as per the essentiality condition under paragraph 34(3)(d) of the CSE Act. In CSE policy, IRTC is considered essential when without the information, CSE would be unable to protect federal systems or SOIs and the electronic information on those systems. However, non-MA acquired IRTC, such as client information, must only be necessary.
(TS) The shared IRTC is also assessed for essentiality to the FI aspect (that is, essential to international affairs, defence or security), for both MA and non-MA cybersecurity information. It is a policy decision to further assess cybersecurity-acquired IRTC for essentiality under the FI criteria, [redacted description of CSE operations].
(TS//SI) As explained by CSE, the cybersecurity-acquired IRTC shared internally in support of the FI aspect is for the purposes of protecting federal institutions or SOIs and the electronic information they contain. This IRTC is used to identify foreign threats to Canadian systems, which aligns with the [redacted related to GC priorities].
ANNEX H: Internal Sharing of IRTC at CSE